Frequently Asked Questions about European Market Email Databases
What is a European Market Email Database Email Database?
A European Market Email Database Email Database is a collection of email addresses and contact information of potential customers and businesses within the European market. It is a valuable resource for businesses looking to expand their reach and target audiences in Europe.
How do the costs break down for a European Market Email Database Email Database?
The costs for a European Market Email Database Email Database may vary depending on the provider, the size of the database, and the level of customization required. Typically, the costs are influenced by the number of email addresses, additional contact information, and any specific targeting criteria desired by the business.
What value can businesses derive from a European Market Email Database Email Database?
European Market Email Databases provide businesses with a targeted and effective means of reaching potential customers in Europe. They can use the database to run email marketing campaigns, promote products or services, conduct market research, and establish a direct line of communication with their audience.
What are the top methods of Online Marketing with European Market Email Database Email Lists?
With a European Market Email Database Email List, businesses can employ various online marketing methods, such as email marketing campaigns, newsletter distribution, personalized offers, product updates, and targeted promotions. These methods can help businesses engage their European audience and drive conversions.
What industries benefit most from European Market Email Database Email Databases?
Various industries can benefit from European Market Email Databases, including e-commerce, travel and hospitality, technology, financial services, education, and more. Any business that aims to expand its reach and target customers in Europe can find value in utilizing such databases.
How can businesses customize their European Market Email Database Email Database?
Emailproleads European Market Email Databases usually offer customization options that allow businesses to target specific criteria, such as location, industry, job title, company size, and more. This level of customization helps businesses tailor their marketing efforts to the right audience and maximize their campaign’s effectiveness.
Why do businesses prefer Emailproleads European Market Email Database Email Databases?
Emailproleads European Market Email Databases are preferred by businesses due to their extensive and up-to-date collection of European email addresses and contact information. The databases are regularly maintained and verified, ensuring high deliverability rates and reliable data for successful marketing campaigns.
Is it legal to purchase European Market Email Database Email Databases?
The legality of purchasing European Market Email Databases depends on the data protection and privacy regulations in the respective European countries. It is essential for businesses to ensure they comply with all relevant laws and obtain explicit consent from individuals before sending marketing emails to them.
Is buying European Market Email Database Email Databases a good idea?
Buying European Market Email Databases can be a good idea for businesses seeking to expand their presence in Europe. However, it is crucial to choose a reputable provider and follow best practices to ensure the acquired data is used responsibly and ethically.
What information does a typical European Market Email Database Email Database include?
A typical European Market Email Database Email Database includes email addresses, names, postal addresses, phone numbers (if available), company details, industry classifications, and other relevant contact information of individuals and businesses within the European market.
Can I get targeted European Market Email Database Email Databases that include Phone Numbers?
Yes, many Emailproleads European Market Email Databases offer targeted lists that include phone numbers along with email addresses. This additional information can help businesses diversify their communication channels and improve customer engagement.
How often can I utilize the European Market Email Database Email Database?
Once you purchase a European Market Email Database Email Database, you can utilize it as per the terms and conditions set by the provider. Many providers offer unlimited usage, allowing businesses to conduct multiple marketing campaigns and stay connected with their European audience regularly.
How can I increase my email subscribers using European Market Email Database Email Lists?
To increase your email subscribers using European Market Email Database Email Lists, you can implement strategies like offering valuable content, exclusive deals, and discounts, optimizing sign-up forms on your website, conducting contests or giveaways, and leveraging social media to promote your email subscriptions. Additionally, sending personalized and relevant content to your subscribers can help retain and grow your email list.
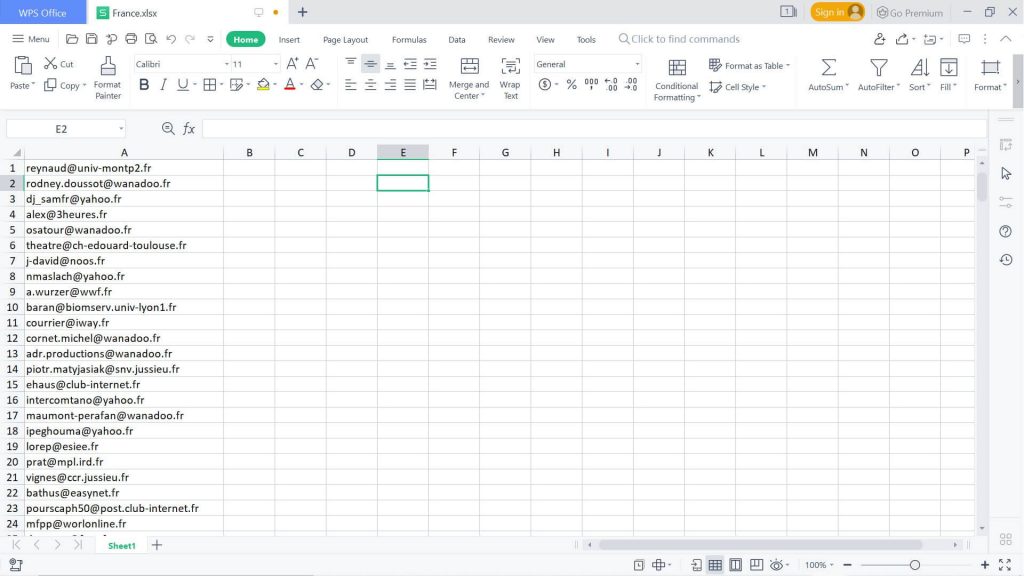
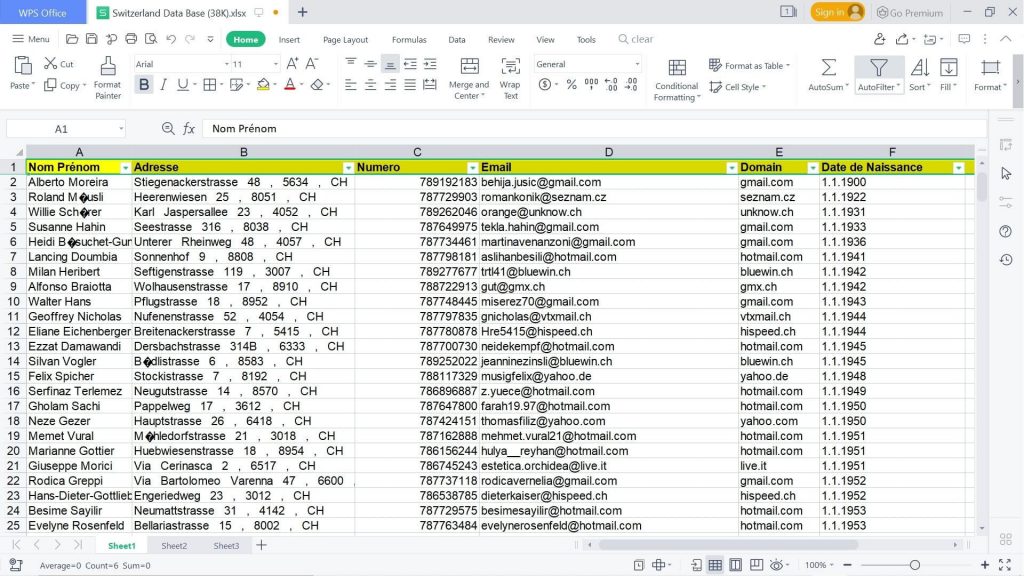
2024 EUROPEAN MARKET EMAIL DATABASE
{1 MILLION lists}
Perhaps you hope to show your company’s products and services to global consumers and need to make valuable business contacts before jumping into the European market.
EUROPEAN MARKET EMAIL DATABASE
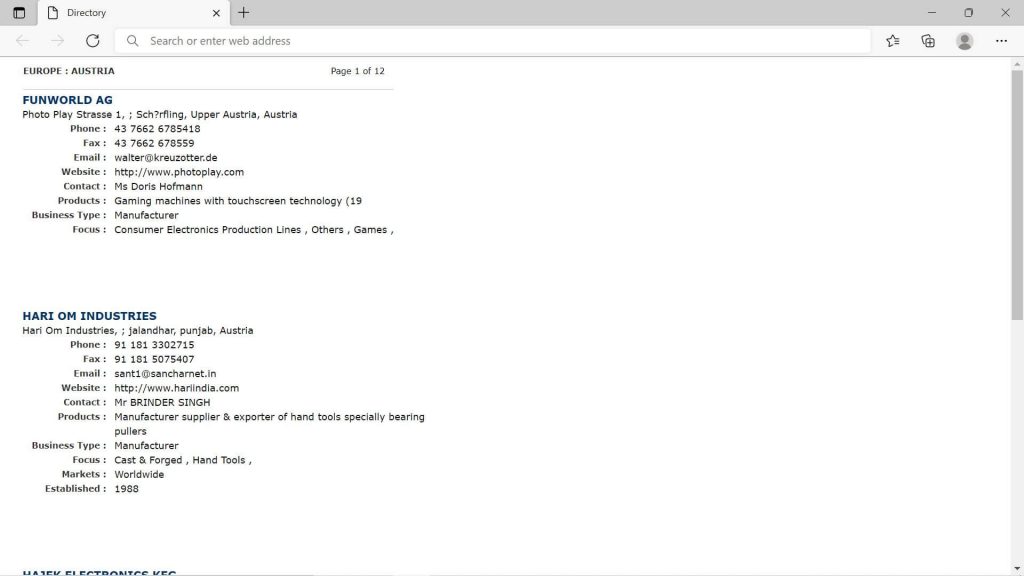
Perhaps you want to find better leads for your next business-to-business (B2B) marketing campaign.
EUROPEAN MARKET Email Lists
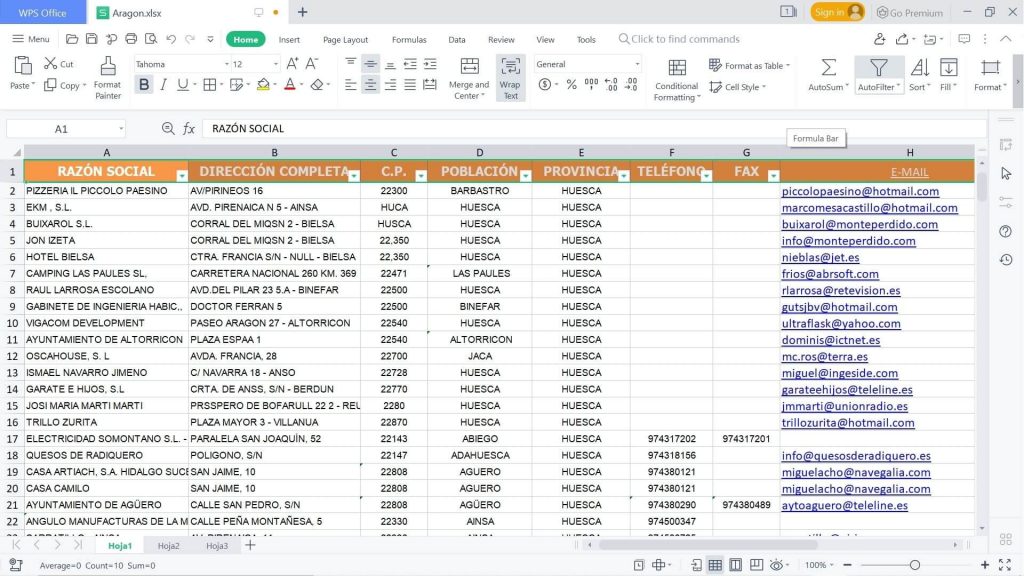
Or perhaps you simply want to network with the top professionals in Europe.
EUROPEAN MARKET Email Leads
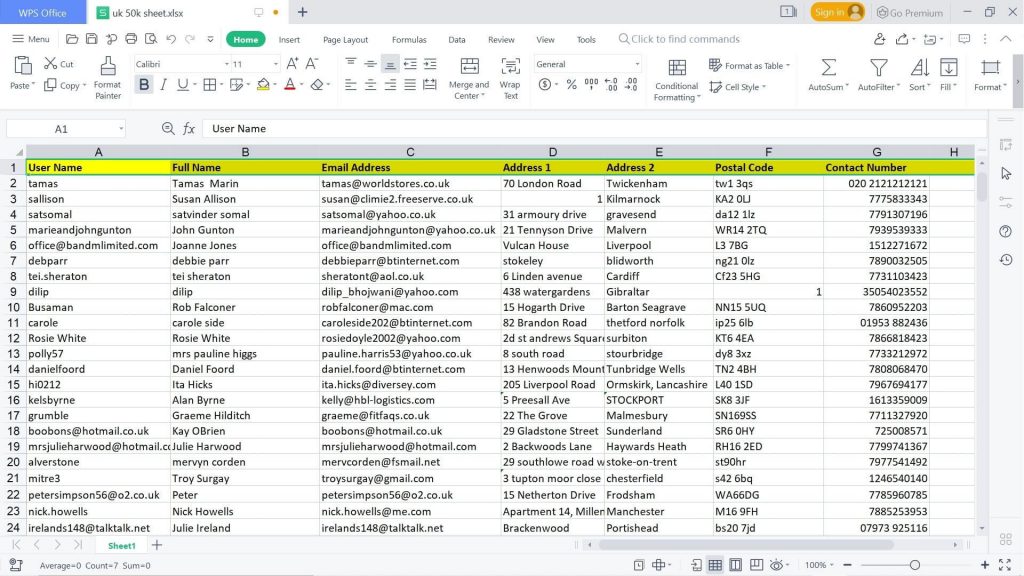
No matter how you want to use this reliable list of accurate contact information, you can boost your sales and make better leads.
EUROPEAN MARKET Mailing Lists
With this pre-made EUROPEAN MARKET EMAIL DATABASE list, which is ready for you to download now, you can find contacts in the following countries:
- Austria
- Belgium
- Czech Republic
- Denmark
- Finland
- France
- Germany
- Greece
- Hungary
- Ireland
- Italy
- Netherlands
- Norway
- Poland
- Portugal
- Spain
- Sweden
- Switzerland
- Turkey
EUROPEAN MARKET Email Address
With Emailproleads.com, it’s easier than ever to reach overseas audiences. You can reach out to business contacts in all of these countries and meet with the key influencers who can further your brand.
EUROPEAN MARKET Business Email Database
EUROPEAN MARKET Consumer Email Database
Today, within minutes, you can download this list, integrate it into your CRM, and start emailing, calling, and writing to these contacts. Pull it and expand your global reach to European markets today!
You Can also learn how email marketing works below (Optional Article below)
What is email marketing?

European Email Database
E-mail marketing, or e-mailing, is a prospecting method used by companies to promote their products or services. This form of telemarketing allows the company to communicate directly with customers without intermediaries.
E-mail marketing can be used to nurture a relationship with leads, convert potential customers, or ensure a good experience for existing customers. Here are some e-mail marketing examples you may have encountered in your inbox.
Welcome e-mails: when a customer interacts for the first time with a company, the latter generally sends a series of e-mails to introduce the company and its products. For example, a computer company offering a free demo of its software will take the opportunity to send e-mails aimed at guiding the customer in his discovery of the program. At the end of the free period, the e-mails will encourage users to purchase the software or subscribe to the service. This highly targeted e-mail is primarily based on the type of offer the prospective customer has responded to before.
Newsletters: newsletters are regular e-mails that generally present the latest company news, and sometimes include links to content from a blog or magazine that may interest the reader. Newsletters are a good way to stay in touch with the market even on a small budget. When a customer responds to an e-mail (for example, by downloading an eBook), the company can forward them to a more targeted list.

European Business Email Database
Reminder e-mails: Companies send reminders to customers who have not completed an action. For example, they can remind customers to complete a transaction after visiting an e-commerce site.

European Consumer Email Database
After-sales follow-up e-mails: after a purchase, the supplier sometimes sends a series of e-mails to better inform the customer about the product he has just purchased. Post-sales follow-up e-mails are especially important if your service is recurring or subscription-based, as they increase customer perceived value and the likelihood of retention. After-sales follow-up e-mails can also be used to sell derivative products or upgrades or benefit from recommendations.
Lead nurturing e-mails: These e-mails nurture a prospect’s interest with content targeted to the problem(s) they are looking to solve. These can be links to blog posts, white papers, or video guides. The purpose of these e-mails is to offer prospective customers useful information, which they will then associate with your brand when they become a customer.
Prospecting e-mails: it happens that a company sends prospecting e-mails to people with whom it has never had contact. This type of message is generally the least effective e-mail format. However, it can give results, especially in a B2B environment and provided it is sent from a personal address and is precisely targeted.
E-mail marketing:

European Email Lists
definition :
The main value of e-mail marketing is that it is very effective without being expensive. Here are some of its main advantages.
Its low cost
Aside from the cost of the software you use, sending e-mails to your address book costs nothing. The return on your investment can therefore only be positive. The Direct Marketing Association has even estimated the return on investment of an e-mailing at
Thirty-six for every euro spent.
Its high efficiency
E-mail marketing allows you to target leads who have already expressed an interest in your business or product. These leads require much less maintenance than those who don’t know you yet. You can also segment prospects and customers based on their needs and interests through audience tracking to understand how they respond to your communications and lead generation campaigns. This will allow you to send them the type of content and offers that are most likely to capture their attention.
Its great flexibility
E-mail prospecting is an extremely flexible tool that finds its place at all sales funnel stages. From the beginning of the buying journey, leads will appreciate the information you offer them to solve their needs. Depending on the type of interaction obtained, you can refine the content you send to them. And, as the prospective customer gets closer to making a purchase decision, you can offer them promotions or discounts to encourage them to take action.
In which case should e-mail canvassing be avoided?
If your main business objective is to increase the volume of targeted customers, e-mailing is not the right solution, in particular, because it is essential to have the e-mail address of a potential customer before communicating with him. It is best to use paid ads, focus on SEO, or post on social media.
E-mail marketing best practices
There are certain best practices to follow in preparing your e-mail marketing strategy. We have identified a few:
Target audience segmentation and content relevance
By segmenting your audience, you can prepare e-mail campaigns whose content will attract the interest of each group. You can qualify each segment according to its centres of interest and evolution in the purchase journey.
Take the example of a seller of domestic or professional air conditioners. This type of company can prepare different campaigns aimed at individuals or professionals.
It can also consider the progress of its recipients in the sales funnel. At the beginning of the journey, customers will probably respond better to the offer to download a catalogue. At the same time, those considering a purchase are more mature and ready to consult your prices or receive a personalized quote.
Automation of the process

European B2C Email Database
Automating the e-mailing process allows you to communicate with your potential buyers at the right time while reducing the manual and repetitive tasks performed by your staff. Configure the actions that will trigger the communications, and your software will do the rest. We will talk more about marketing automation at the end of this article.
Follow-up and changes
E-mail prospecting is not an exact science. Some elements will have the expected results, and others will not. Most commercial e-mail solutions offer data and analytics tools to help you optimize your campaigns.
If one of your e-mails isn’t getting the open rate you expect, consider editing the subject or changing the time of day it sends. If a message’s click-through rate isn’t high enough, change the presentation or call-to-action (CTA).
One of the best solutions to improve your e-mailings is to go through an A/B testing phase. This involves creating two different versions of the same e-mail and sending them to two samples on your list to see which is more effective.
A/B testing is especially common for those looking to increase their open rate. Write two different subject lines for the same e-mail, send both versions to the same number of customers, and immediately find out which one encourages recipients to read the e-mail. All you have to do is choose the item with the best result for the rest of the campaign. You can test calls-to-action (CTA), send schedules or offer types in the same way.
Do not send unsolicited mail
It can be tempting to bomb your entire list frequently. This is how you become a spammer. Just send information to those who will find it truly useful, based on their needs and progress along the purchase path.
How to choose e-mail marketing software?

European Email Leads
With all the marketing and e-mailing products on the market, businesses are spoiled for choice. To find the right one for your business, consider several factors:
The size of your list and the volume you plan to send
E-mail marketing providers usually offer several solutions depending on the size of your database and the volume of e-mails you plan to send. Be sure to choose the one that best suits your business goals. If you want to expand your list, check that your software will meet your future needs.
Is the software compatible with the other tools you use?
Your e-mail marketing platform should seamlessly integrate with your workflow, including in the following ways:
By working in parallel with your CRM software, the software can access information about your customers.
Good integration with your inbox (e-mail client) will allow you to import your contacts automatically.
By accessing data from your e-commerce site, the software will allow you to send e-mails to customers who have abandoned their carts.
Is it so difficult to create a successful e-mailing?
To create a successful and effective campaign quickly, you need a good tool. Some software comes with preconfigured e-mail templates if you lack inspiration. If you prefer a higher degree of control, e-mail design wizards let you insert, move, and delete elements at will.
Does this software have other functions?
Many promotional e-mail solutions offer additional features to help you prepare effective campaigns. You’ll find software to help you prepare landing pages, create lead generation forms, and analyze results in depth.
The rates

European B2B Email Database
Price is an important factor. To ensure a positive ROI in your business efforts, you need to choose a cost-effective solution that contains all the features you need.
Conclusion
What is e-mail marketing? E-mail marketing is a prospecting method used by companies to promote their products or services.
Why use e-mail canvassing? E-mail marketing is economical, effective, and adaptable to all levels of the buyer’s journey.
- Best e-mail marketing practices:
- Segment your contact list to send only perfectly targeted content.
- Automate your processes to avoid sending spam.
Monitor results and modify your e-mails to optimize the performance of your campaigns.
How to choose e-mailing software? Choose a program that offers the features your teams are looking for. Be sure to choose an appropriate solution for the volume of your list. Consider what other software you use and the level of integration offered.
What is automated e-mail marketing? Some e-mail marketing solutions offer automated processes. This is a great way to prepare effective campaigns while reducing manual tasks.
How to Design your Email Marketing Strategy for 2024

European Business Email Lists
Introduction
A successful email marketing strategy requires a lot of planning and a lot of thought. By taking the time to plan an email marketing plan you can achieve your objectives more efficiently and develop the most successful campaigns you can.
This guide will outline what you need to think about when planning your campaign. It also provides you with an in-depth illustration of the strategy of an email marketing campaign working and questions to aid you in making the most value from all your efforts to market.
Each successful marketing email strategy begins with a strategy
How do you come up with an effective email marketing strategy? It is important, to begin by making a plan prior. You can ask these questions:
- What’s the point of investing in email? What are the business outcomes you hope to be able to
- Who are the readers who be able to read it?
- What are they expecting to be expecting to
- What is the definition of “success” in this particular project?
Before you begin creating emails or thinking about ways to improve the subject lines of your emails first, you must answer these questions. You aren’t likely to be with an elegantly designed email that is only noticed by software that filters emails.
To be noticed in the first place, you need to develop effective email campaigns. In order to do this, we’ll walk you through the fundamentals that you must apply to create an effective strategy for marketing via email for 2024.
A full description of the strategy for an email marketing campaign
Let’s begin the process by reviewing the Modern Henchperson magazine’s strategies for email.
Okay, we have come up with the idea. But, bear with us, as this strategy will help you determine the strategy you’ll use that you can implement for the next time.
Imagine if there was an issue of a magazine that focuses on today’s busy supervillain. This supervillain doesn’t have time to conduct basic maintenance on death traps. They’re not able to take care of their Homeowner Association because their volcano cave is “not up to par.”
They hire a henchman. Henchmen must be in a state of continuous improvement in order to perform the job a henchman must do: shoot guns in a way that is inaccurately directed toward James Bond, fill gas in the submarine, and burst out into wicked laughter when the time is right.
Now, imagine you’re developing an email marketing plan to promote Modern Henchperson Magazine. You’re familiar with your target audience The henchman who is busy. That’s about it in the present. Use the below template to inquire about the marketing strategies for email which will inform all your actions:
The Modern Henchman Magazine email marketing strategy document
The target audience: Who do you send the emails to?
- Current subscribers to the magazine in print
- The people who signed up to receive emails by filling out a form to sign up or landing pages on your site
- Customers who have purchased through our website
Why is this the primary reason behind such emails?
- To boost sales for Our Modern Henchman line of products by encouraging customers to purchase for the first time, and by converting readers into repeat buyers
What kind of emails do you plan to send?

European Business Email Leads
- Newsletters to customers
- Subscription reminders
- Purchase receipts and invoices
- Promotional emails
- Re-engagement emails
- Welcome emails
What kind of content do want to share?
- Special deals
- In-depth articles on the subject that connect to our products
How often will you send out emails?
- This newsletter is distributed each month. It will also include additional reminders and notifications according to the requirements
Have you got a current visual design that you’d like to see your email match?
- Yes, the site is modernhenchman.com
Have you got any examples of email marketing strategies that you enjoy?
- Amazon’s brand new product emails
- Baskin-Robbins Customer loyalty email messages
This is a great place to the beginning. Let’s say that you have recognized the need to remain current with your current subscribers and previous purchasers. They are, after all, those who are most likely to buy their products in the near future. Therefore sending emails or follow-up offers to customers at least each month, either once or twice is a cost-effective way to keep in contact with customers.
It also keeps them in its customers’ minds, ensuring that, when they need a freeze ray or an exploding hat, modernhenchperson.com is their first stop.
Once we have our outline and a plan, we can begin to figure out what is required in order to finish the task. First, we need to establish the specifics of what a successful project should take.
How do you set goals for email marketing

European Consumer Email Lists
With your brief in hand now is the time to begin setting your goals. What are the indicators you use to determine an effective email marketing campaign?
The key to success is having a clear objective in mind. This is just as important when it comes to email marketing as for any other online marketing strategy.
If you have your answers from the brief that you were given then you can summarize them as specific goals. The goals must be as specific as possible.
If you’re looking to boost sales for print subscribers and turn new customers from subscribers who only receive emails to customers who are active. It’s a good starting point but you should look for more specific objectives.
For instance, what is the meaning of “increase the sales”? Do you think it is enough to get only one additional sale? This may sound like a joke however there are items and services that one sale can provide a full year of email marketing strategy.
If you offer consulting services, like with thousands of dollars each hour, it’s a lot different from selling web 2.0 gradient stickers at a dollar per box. You must be specific and precise in order to establish goals that are useful.
If you’re uncertain about the value, you can set out your goals in terms of the number of people arriving at your site via hyperlinks in the email. If you are aware that 1.8 percent of web visits result in a sale and you know how many people come to the site via email could be transformed into a dollar amount.
For the modern Henchmen For Modern Henchmen, we could recommend this as the principal goal: to generate a minimum of $400 in direct sales from subscribers of newsletters in the initial week after each email that is sent.
Or, you may not have a mission that is specifically tied to a financial return. In some cases wanting to get a response from the reader could be precisely the goal, they’re trying to reach. Here are some more examples of goals to think about:
- Contact five of our former clients
- 44% of users are open to the email
- 20 percent of subscribers have clicked at most one link
- 30 people visit this particular page on the website
They can be easily tracked, so you can determine the moment you’ve reached them. Sometimes, this won’t be feasible. For instance, it could require years to convince a client to decide to buy an entire Warehouse layout or Mainframe. The goals to be measured in these situations could be about maintaining relationships, and the measure is the number of emails received from the client.
This is more than just achieving targets. It also encourages you to think about the reasons behind sending these messages in the first place. Sending emails with purpose and focus are those that stand out. all the rest are just noise that clogs the inboxes.
Email metrics: how do we determine the success of our email campaigns

European Consumer Email Leads
If you’ve got some or all of your goals set It is time to establish the necessary tools or processes to determine if those objectives have been accomplished. It could be the sales numbers from a particular department, reports from your email provider, or statistics from your website.
If you’re using special software (whether external or internal) to send out emails, a large portion of these metrics could be made available to you in the software package. The types of numbers that you should be able to track include:
Open rates
What percentage of those receiving the mail actually perused the email? The number can be calculated by observing the download of the tracking images in every email. However, many email programs do not download images automatically, and therefore not every email opened can be tracked. Additionally, some email programs display only plain text with no images downloaded.
Note: While open rates may still be an important metric but Apple’s Mail Privacy Protect feature has rendered them increasingly not reliable. Instead of relying on open rate data to gauge the success of your campaign, we suggest shifting to other engagement metrics, such as the ones listed below.
Rates of click-through (CTR)
What percentage of those who received the email actually clicked on the link? Most email services will redirect every link to their own tracking services to track clicks.
Forwards
What percentage of people have actually utilized the “send to an individual person you know” option to share an email? (We’re going to assume that your software comes with this feature.)
Unsubscribe
How many people choose to unsubscribe from future emails by using the software’s built-in unsubscribe option?
Conversion rate
What percentage of people who clicked through on your ads went to buy something or download a trial version, or do any other action you could keep track of? Software such as Google Analytics can be used to track these actions and link them to specific sources, like your email marketing campaigns.
The most important measure isn’t just the raw numbers but the variation in the numbers between one campaign and the next (also known as”trend”). After each campaign is sent we’ll make changes to the strategy for marketing emails design and content, and even to the time of the week and the time of the day when you send emails. The previous measurements will determine if the modifications are working or not.
It’s time to realize that you’ve established goals for your email marketing strategy and are able to determine whether we’ve met the objectives. Now is the time to begin creating a strategy for the HTML email.
Emails are designed using the same technology as websites: HTML and CSS. But, there are many distinct aspects regarding what constitutes a good design strategy for email.
Strategy for content: What content are you going to tell them?
It’s tempting for web developers to imagine HTML emails as being a simple website. It’s only HTML and CSS in the end. In addition, a large number of users might be using an internet browser.
This is all true. However, emails and websites are two different types of media. As print designers needed to adapt to the specific limitations and possibilities of the internet Web designers who work with email must also change their approach to thinking.
Making sure your content is optimized for the appropriate medium is often a great way to turn ordinary emails into excellent ones.
A reminder email is not a website.
We tend to consider websites as online storefronts. Visitors are constantly coming to our site either directly, through searching, or following an online hyperlink. When someone comes to your website, they typically already have an idea of what they’re looking for. In terms of visuals, your site is displayed in a large browser window.
Emails are a distinct situation. Your inbox can be more like your home than a shopfront. You receive emails without taking action. Once they are delivered to your inbox, the area that is visible in the email could be a fraction of the size of a browser’s window.
Lorem ipsum
Beware of using the lorem ipsum wording as a filler text in spite of the fact that it’s a common practice for web design. A lot of emails (and too numerous websites) were designed with placeholders that have turned out to be completely different in terms of length style, design, and form in comparison to the content. The design was then required to be redesigned, long after it had been completed.
How often should I send emails?
There’s no definitive solution. However, in general, you should avoid sending too many emails in your email marketing plan instead of too many.
According to the data from 2019 around 50% of your subscribers believe you’re sending frequently. 45.8 percent of respondents mark emails as spam when companies send out too many campaigns. Furthermore, when asked about ways companies might improve their emails campaigns, 43.9% suggested sending messages less frequently.
What is the ideal timing to mail an email?
This question’s answer is easy. When do your customers typically go through their emails? The answer is simple.
It is important to send emails only when you are able to be sure that your customers are on their phones or mobile device. When you mail an email during the night, for instance, you can be sure that it will be lost among a plethora of other emails when subscribers check their phones at the beginning of the day.
Based on our study from Campaign Monitor, email opens begins when people begin their day and last throughout the day, before easing off late into the night. 53% of emails opened are made between the hours of 9 a.m. between 5 p.m. and 24% happen during the time between p.m. between 6 p.m. and 11 p.m. as people settle in for the night.
It’s best to break your list into parts based on geolocation (time zones) and then send emails at the subscriber’s preferred time.
Also, you must consider your content and audience. Certain kinds of content work well for an early Monday morning appearance such as a list of henchman “weekly suggestions,” for example. Some are more suitable for campaigns after hours, such as happy hour specials.
Do I need to purchase an email address?
No.
There are many products and services that claim to offer fully updated databases that are opt-in however, there is no way to verify that. The majority of email service providers and anti-spam programs have a dim view of lists purchased from email providers. It is possible to have your IP address for sending flagged as spam and permanently damage the reputation of your sender.
The world’s governments are also taking the security of data more seriously. In the future post-GDPR environment there is a chance that you will face costly legal fees and fines for sending out emails to people who have not given permission to communicate with them.
Try a slower method of creating your own opt-in lists in time. You’ll not only avoid legal problems and spam filters and legal issues, but you’ll also get more effective campaign results.
What is an acceptable open rate?

European Consumer Email Leads
There’s no definitive answer to this since open rates differ according to a variety of variables. Every industry, for instance, is a particular one, that has its own open rate.
Based on our findings on the Campaign Monitor According to our research with Campaign Monitor, the typical open rate for all industries is between 20% and 40 percent. This was the case in 2020. Our benchmarks for an email in 2021 saw 18%. This means that 20% might indicate that you’re doing better than the norm. Every industry is unique. Don’t forget that as you add more companies to your list and your list grows, the possibility is that your open rate could drop by a small amount.
A few to increase the effectiveness of your email marketing campaigns. open rates:
- Keep your email subject lines brief and smart
- Make use of marketing automation and segmentation to deliver more relevant emails at the appropriate time.
- Take into consideration removing those subscribers who are not active from your subscriber list.
- Be sure to conduct the a/b test every time you are able to.
How many clicks can I be expecting?
This is a follow-up to the earlier question but is more likely to give a precise answer. Industry reports on email marketing strategies generally state the 2-11% unique click-through rate as the norm.
Similar to open rates, typical click rates differ based on sector. Niche hobbies for instance typically have more click-through rates than those of vitamin and supplement businesses.
Other elements can also affect the effectiveness of your click-through strategies for marketing via email. Email newsletters that are standard are less effective in terms of click-through rates, which are approximately 3.48 percent across all industries. However, the rate has dropped in recent times and has risen to 1percent.
How can I stop my email from being filtered?
The majority of the time it’s the content, and perhaps the “From” email address, that the filters are looking at.
The best way to start is to stay clear of spammy words, then evaluate your mail marketing strategy using the most diverse clients and filters possible.
Making your content as personal as you can aids in avoiding spam filters. Split your list into various groups based upon preferences, age, gender as well as location details. Make distinctive content for each group of subscribers.
Don’t send emails that include one image with no copies. Spam filters will be able to detect these kinds of emails.
Which email marketing tool do I intend to use?
The process of selecting an email marketing tool can be a challenge. There are many choices to pick from, and many of them claim they have similar features. what are you supposed to do to decide?
We’ll admit that we’re biased, we believe that Campaign Monitor is a top option for those looking for an effective, yet simple-to-use marketing tool via email.
Created by email marketers to help email marketers, Campaign Monitor is a powerful tool that allows advanced features for email marketing easily accessible to everyone. Some of the most requested features are:
- Drag-and-drop email builders
- 80+ mobile-friendly, free email templates.
- Advanced, approachable email automation
- Tools for personalizing and segmenting lists
- Signup form creator
- A team of support and deliverability you can trust
Marketers across the globe from small-scale businesses to professionals in eCommerce to non-profits and agencies utilize Campaign Monitor to send better emails faster. You can begin today for free.
Wrap Up
Marketing can be a challenge, and it involves many unidentified factors. With a comprehensive plan, you’ll be able to retain certain aspects of control.
A well-planned email campaign strategy allows you to track the results and measure metrics that translate into actual figures. As with all aspects of marketing, planning is vital for getting the greatest outcomes. Make sure you are in control of your long-term strategy for email marketing by creating a campaign calendar. We’ve prepared an extensive guide with lots of ideas to help you get going.
We assure pleasant email addresses in compliance with standards
We act by current regulations on privacy and personal information processing to provide you with established and one hundred% steady electronic mail lists.
How we accumulate records
We deal with each piece of data in our electronic mail database with the utmost precision: we continuously test and verify that each email addresses are lively and up-to-date, in compliance with all legal privacy guidelines in pressure in Spain and the European Union and with unique Attention to the General Data Protection Regulation (RGPD).
1. We do not have personal song records that may be attributed to people, but the simplest facts of prison entities
2. We hold all statistics in the European Union solely the usage of records centers positioned in Italy and France
3. The processing of company statistics is sometimes restrained by using the GDPR; the purpose of that is to defend private records.
Where do the records within the database come from?
Are you focused on the BTOMAIL email?
BTOMAIL only approaches public facts of criminal humans, businesses, and experts: according to the GDPR recitals, these statistics can be used for advertising and marketing purposes even without express consent, in contrast to data relating to natural persons, which require express consent.
In this manner, we ensure that our customers’ email deals with databases fully comply with privacy and facts processing legislation.
Our email database consists of Spanish corporations or professionals who have freely indicated their contact details (digital or not) in public directories.
Your records come from online resources, including websites or social debts, and while constructing our email lists, it is decided on and selected using algorithms designed via our IT group, algorithms similar to those used by Google and other search engines.
Are you searching out excessive conversion? Client email lists? Do you want to target new capacity customers or make your patron base bigger? Then you’ve got landed on the right page. At BuyEmailMarketingLists.Com, we offer highly nice patron electronic mail databases giving you the right of entry to thousands and thousands of international customers. You can filter the statistics using the start date, gender, metropolis, and other to-be-had facts.
All B2C Email Lists available at BuyEmailMarketingLists.Com are decide-in.
As the marketplace pioneer in B2C email advertising and marketing lists, we will provide a correct and up-to-date consumer email database in 2024 so you can increase your sales and lead-era campaigns. Our statistics collection group collects leads for our new email lists from target customers from multiple assets, including choose-in web forms, phone calls, well-known shows, alternate indicates, public surveys, online contests, sweepstakes, and advertising websites—membership, and various techniques in which the recipient gave their email deal with and called records. Our lists assure extreme accuracy so you can handle deliverability. With self-assurance, you can send email campaigns to our customer email database, so you get high open and click-on costs from your electronic mail marketing campaign.
Every time you buy a brand new consumer email database from BuyEmailMarketingLists.Com, you have our full guarantee that you’ll get an excessive ROI. Whether you’re a new or established commercial enterprise, whether or not your audience is consumers, our newly up-to-date customer mailing list will get you off to a great beginning. We offer new patron electronic mail leads from countries all over the globe.

Fresh, Up-to-Date Lists: Our purchaser email lists include up-to-date facts often checked for validity and accuracy.
High Deliverability: BuyEmailMarketingLists.Com’s patron email database has excessive deliverability and one of the lowest soar charges.
Affordable Consumer Emails: We offer the most competitive and affordable client email lists amongst our competition.
High Open Rate: Our new email database guarantees higher available prices than email lists from our competition.
Email database: advertising and marketing on the carrier of your commercial enterprise approach
“Gold is within the listing”: communique and advertising are the keys to the achievement of a commercial enterprise. However, a profiled and certified email database is a gold mine to get new customers and gain visibility. Email Marketing is a good device for a successful and developing corporation to draw new corporations or experts and speak with them through reading the outcomes of the movements.
enterprise-approach
commercial enterprise-approach
Acquire a database of email addresses for selective prospecting
Whatever your enterprise, buying an email database is a winning device to boost your advertising. With centered statistics, you save valuable time and feature the possibility to locate and engage customers with only some clicks. Through Bancomail, you may select the leads that are primarily based on your goals. Our multi-channel databases, prepared with several extra data on businesses, including the range of employees, turnover, or social channels, are a special tool for accompanying you from prospecting to submit-campaign follow-up.
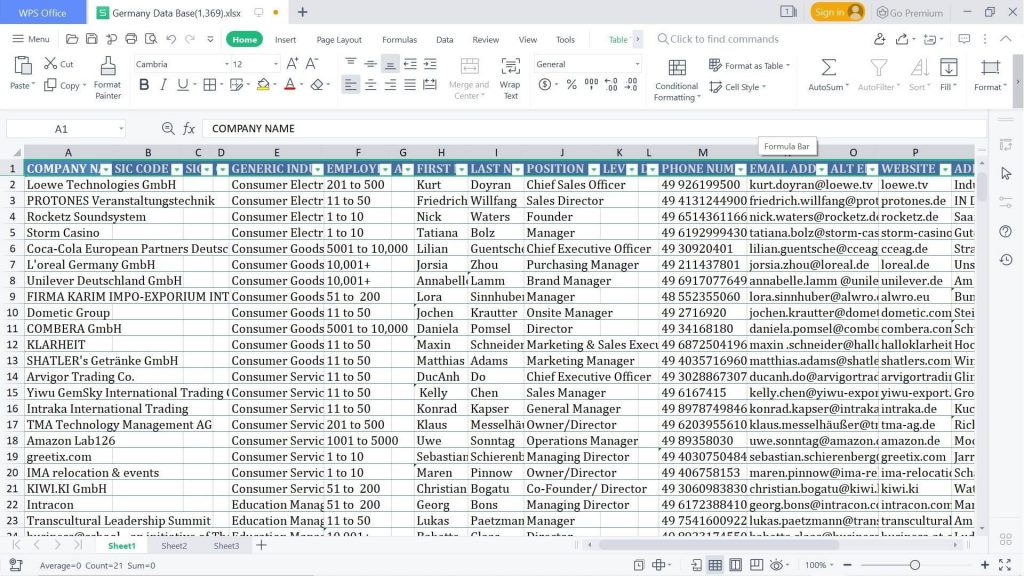
THE Germany Top Executives Email Database helps guide both German agencies and yours! Once you purchase this database, you’ll have a wealth of valuable sales leads at your fingertips. This isn’t just a widespread list of capability customers; it’s miles full of real names, identities, enterprise categories, phone numbers, email addresses, fax numbers, and business enterprise info that you could use to make direct contact with the maximum essential for advertising. Bell. Our Germany Top Executives Email List is gadget scanned and human-tested for accuracy, so you may not waste time sending messages that don’t reach their supposed recipients.
The contact classifications on this electronic mail listing of Germany’s top executives include Group President, Group Chief Executive Officer, Group Managing Director, Area Manager, CEO & Managing Director, President & President, President (Partner), Director of Country, Country Manager, Vice President, General Director, Executive President, Executive Director, Financial Advisor, General Manager, Human Resources Coordinator, Managing Director, President and CEO, Vice President, Vice President, and so on.
statistics to be had
Name – 10,123
Last call – 10,123
Job role: 10,123
Email address – 10,123
Company name – 10,123
Business class: 10,123
Employees – 10,123
Annual earnings: 10,123
Website – 7,879
Address – 10,123
ZIP Code – nine,541
Telephone – 7,289
City – nine,632
Country – 10,123
The Czech Republic electronic business mail list, consists of email addresses of human beings in the enterprise category within the Czech Republic. This B2B email listing we offer you is a lively electronic mail advertising list for your enterprise. If you need to buy the Czech Republic business email address database, we suggest you buy this.

information to be had
Contact character – four,404
Company call – 1,892
Address – 4,398
Telephone – 3,755
Fax – 781
Email address – 5,024
Website – four,401
City – 2,495
Country – 5,024
$58
$29
The Czech Republic enterprise electronic mail listing consists of electronic mail addresses of humans within the commercial enterprise category within the Republic.
Purchase also: France Email Database [2024]















Reviews
There are no reviews yet.