4.5 Million China Email Lists : Business and Consumer Address
In an era where digital communication is paramount, acquiring a China email list has become a cornerstone for businesses looking to expand their reach within the world's most populous nation. Emailproleads stands at the forefront of providing comprehensive email lists, ensuring that you can buy email lists in China that are curated to drive your business's marketing strategies and communication forward.
Navigating the vast digital landscape of China, with its booming economy and expansive business opportunities, necessitates a robust and strategic approach to communication. A China email list is a valuable asset for any business looking to make inroads into this lucrative market. In this era where data is king, having access to a comprehensive database like the one offered by Emailproleads.com can be a game-changer for businesses worldwide.
Are you looking for an effective way to expand your business reach in China? Look no further! Emailproleads offers a comprehensive China email list that can help you achieve your marketing goals. In this article, we will delve into the world of email lists, where to buy them, and how they can benefit your business in various states like Shanghai, Beijing, and Guangzhou.
What is a China Email List?
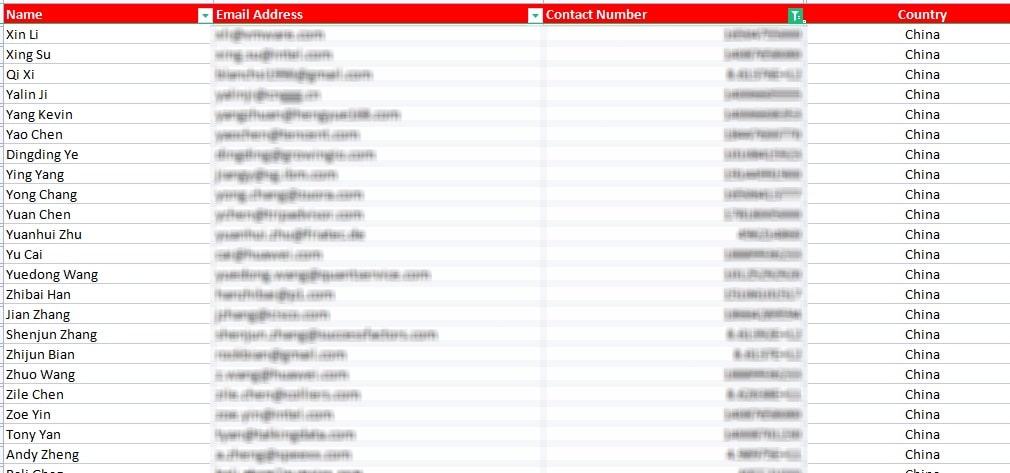
A China email list is a database containing a collection of email addresses from individuals and businesses in China. This list is a valuable resource for businesses looking to connect with their target audience in China. It includes email addresses from various states across China, such as Beijing, Shanghai, Guangdong, and more, ensuring you have access to a wide range of potential customers.
Targeted China email list - Your Gateway to the China Market.
A China email list is an aggregation of email addresses from individuals and businesses across various provinces such as Guangdong, Zhejiang, and Jiangsu, among others. These lists are valuable tools for targeted marketing campaigns, facilitating direct communication with potential customers and partners within China. Emailproleads prides itself on offering up-to-date and verifiable lists to help you connect with your desired audience effectively.
Emailproleads.com specializes in compiling email lists that are not only extensive but also conform to the highest standards of quality and relevance. Their databases are meticulously verified and updated to ensure the highest level of accuracy and deliverability, making them an indispensable resource for any business strategy.
Can You Buy Email Lists in the China?
Yes, you can indeed acquire China email list. Emailproleads offers a streamlined process to obtain these lists, ensuring they are compliant with local regulations. With their expansive and regularly updated database, finding a reliable source for your marketing endeavors is just a click away.
Emailproleads.com emerges as a trustworthy source for acquiring a China email address list that respects the legal framework and ethical considerations of email marketing. They provide lists that are obtained through lawful means and are intended for companies looking to establish legitimate connections with their target audience in China.
Yes, you can! Emailproleads offers a reliable platform where you can buy email lists in China. Our extensive database covers various industries, job roles, and geographical locations, including Inner Mongolia, Hubei, and Shaanxi. We understand that each business is unique, and our customizable email lists allow you to target your specific audience, ensuring maximum ROI.
China Email Address List
For businesses looking to target other businesses in China, Emailproleads offers a specialized China business email list. This list is ideal for B2B marketing and includes contact information for decision-makers, executives, and professionals in various industries. Whether you want to expand your network, explore new partnerships, or drive sales, Emailproleads' China business email list is your key to success.

Unlock Business Potential with Our Comprehensive China Email List - Your Gateway to Targeted Marketing and High-ROI Campaigns in China's Dynamic Market!
Are you looking for a more refined approach to your marketing efforts? Emailproleads also offers a list of email addresses in China. Our data includes email addresses of professionals and decision-makers in key industries, such as technology, finance, and manufacturing. With our China email address list, you can target your audience precisely, whether you are in Chongqing, Anhui, or Jiangxi.
Where to Buy China Email Lists?
The quest for trustworthy and comprehensive email lists leads many to Emailproleads, a provider that stands out in the market. Their lists are meticulously compiled, giving businesses the boost they need in the digital realm by connecting them with key stakeholders across China.
Emailproleads.com stands out as a provider of choice for businesses seeking to procure a China email address list. They offer a diverse range of lists that cater to various industries and are customized according to the business requirements. With their commitment to data accuracy and customer service, Emailproleads.com is your go-to destination for email lists that can give you a competitive edge in the Chinese market.
Where Can I Get a Free List of Email Addresses in China?
For those looking for a China email address list for free, Emailproleads occasionally offers samples of their exhaustive email lists. This allows businesses to experience the quality of the data before committing to a purchase.
With the digital economy in China booming, an authentic email directory can serve as a powerful tool to tap into the vast market. Provinces like Guangdong, Jiangsu, and Zhejiang, which are industrial powerhouses, could become accessible through such a list. As businesses often seek a no-cost solution initially, Emailproleads.com's sample offering is a smart strategy to attract potential clients by showcasing their expansive and meticulous database.
China Business Email List
Acquiring a new business email list in China can catapult your B2B interactions, providing direct channels to engage with industry leaders and decision-makers. Emailproleads's lists are a goldmine for networking and building professional relationships within the Chinese market.
By utilizing such a specialized list, businesses can enhance their B2B marketing strategies, ensuring that they connect with the right stakeholders. Emailproleads understands the pulse of China's economic landscape, offering a directory that is not just a list of contacts but a bridge to meaningful business relationships. The lists are regularly updated to ensure accuracy, providing businesses with a reliable resource for their email marketing campaigns.
For businesses looking to connect with other businesses, our China business email list is the ideal solution. We offer a wide range of filters, including job roles, industries, and company sizes, making it easier for you to target B2B contacts in China. Whether you're in Ningbo, Hunan, or Jilin, our business email list can help you establish lucrative partnerships and collaborations.
China B2B Email List by Job Roles
Specificity is key in B2B marketing, and that's why Emailproleads offers a China B2B email list segmented by job roles, ensuring your campaigns reach the right desks, from CEOs to HR managers.
For those wondering "Where can I get a B2B email list in China?" - the answer lies in Emailproleads.com's segmented directories. Their targeted approach ensures that promotional materials or partnership proposals land in the right inbox, significantly improving conversion rates.
| Job roles | Phone number | |
|---|---|---|
| CEO | 29962 | 29963 |
| CFO | 29962 | 29963 |
| CTO | 29961 | 29964 |
| Manager | 29963 | 29962 |
| Accountant | 29963 | 29962 |
| Software Developer | 29964 | 29961 |
| Marketing Specialist | 29964 | 29961 |
| Sales Representative | 29962 | 29963 |
| HR Coordinator | 29961 | 29964 |
| Operations Manager | 29964 | 29961 |
| Project Manager | 29963 | 29962 |
| Graphic Designer | 29961 | 29964 |
| Data Analyst | 29964 | 29961 |
| Customer Service Rep | 29962 | 29963 |
| Quality Assurance | 29963 | 29962 |
| Researcher | 29961 | 29964 |
| Logistics Coordinator | 29964 | 29961 |
| Public Relations Officer | 29962 | 29963 |
| Business Analyst | 29963 | 29962 |
| Legal Advisor | 29964 | 29961 |
| Total | 599265 | 599264 |
Where Can I Get a B2B Email List in the China?
Look no further than Emailproleads for a comprehensive B2B email list in China. Their resourceful lists are an asset for any business looking to target professionals based on their job roles and industries.
For those wondering "Where can I get a B2B email list in China?" - the answer lies in Emailproleads.com's segmented directories. Their targeted approach ensures that promotional materials or partnership proposals land in the right inbox, significantly improving conversion rates.
China Company Email List
Compiling a China company email list can be a Herculean task, but Emailproleads simplifies this by providing an extensive database of email addresses from companies across China's sprawling industrial landscape.
The B2B lists from Emailproleads cater to various industries and are designed to streamline the process of finding the right contacts in this vast market. With their comprehensive list, companies can save time and resources that would otherwise be spent in researching and compiling contacts.
The China company email list offered by Emailproleads is a valuable resource for businesses looking to establish connections with other companies in China. Our database is regularly updated to ensure accuracy and relevance. Whether you're interested in reaching out to enterprises in Anhui, Jiangxi, or Liaoning, our company email list can help you build meaningful partnerships.
China Industries List
Understanding the different industries in China can be complex, but with Emailproleads, you can receive an organized China industries list, ideal for segmenting your marketing efforts according to industry-specific dynamics.
Whether it's a startup looking to source materials from Hebei's industrial sector or a software firm aiming to collaborate with corporations in Shanghai's financial district, Emailproleads provides an invaluable resource. Their China company email list is not just a random assortment of emails; it's a strategic asset, regularly refined to ensure that your business communications are effective and yield fruitful results.
China is home to a diverse range of industries, from manufacturing to technology and finance. Our China industries list allows you to target specific sectors and businesses in locations like Inner Mongolia, Gansu, and Tibet. With this specialized data, you can tailor your marketing campaigns to suit the needs and interests of your target industries.
China Consumer Email List
Tapping into the Chinese market requires a nuanced approach, and a China consumer database download from Emailproleads gives you access to a wide array of consumer emails, refining your B2C marketing strategies.
As the world's most populous country, China's consumer market is incredibly diverse. From the bustling metropolis of Beijing to the tech hub of Shenzhen, each region holds distinct consumer behaviors and preferences. Emailproleads recognizes this variety and offers China B2C email lists that are meticulously tailored to align with your marketing needs, allowing for targeted campaigns that speak directly to the consumer's interests.
The value of a targeted email list lies in its relevance and accuracy. Emailproleads ensures that the consumer lists are not only extensive but also compliant with data protection standards, which is crucial for entering a market as regulated as China's. Their lists include a variety of demographics, from young urbanites in Shanghai to the growing middle class in provinces like Jiangsu and Zhejiang, giving businesses the edge in a competitive digital landscape.
China B2C Email List
The China B2C email list from Emailproleads is a vital resource for businesses aiming to connect with Chinese consumers directly, enhancing the impact of their promotional efforts.
The attention to detail is evident in the segmentation of the lists. They not only categorize consumers based on common demographics but also include specialized segments like China zip code email lists, enabling businesses to perform hyper-localized marketing campaigns. This level of detail ensures that marketing efforts are not dispersed but are targeted, which in the context of China's vast and varied landscape, can mean the difference between a successful campaign and a missed opportunity.
For businesses interested in business-to-consumer marketing, Emailproleads offers a comprehensive China B2C email list. This data includes email addresses of individual consumers in regions like Jiangsu, Shandong, and Hubei. Whether you're promoting products or services, our B2C email list is a powerful tool for reaching your target audience.
China Zip Code Email List
A free zip code China email list enables a geo-targeted approach to marketing. Emailproleads's data includes detailed segmentation, allowing for precise targeting based on locations.
Having a zip code level email list at your disposal means that your marketing campaigns can be as specific as targeting consumers in a particular district or even a street. This specificity is particularly beneficial for local businesses or international enterprises looking to create a local impact. By using these hyper-local lists, companies can customize their messaging to fit local cultures and trends, which in China, can vary significantly even within the same province.
Emailproleads provides access to a meticulously curated China zip code email list. This data is a valuable resource for businesses seeking to localize their marketing efforts. By targeting specific zip codes in China, you can tailor your campaigns to address the unique needs of each region.
Buy China Email Database
Businesses looking to make inroads into the Chinese market can buy China email databases from Emailproleads, which offers a wealth of data to help create meaningful connections and foster business growth.
When you purchase an email database from Emailproleads, you’re not just buying a list of emails; you're investing in a resource that can transform your business's outreach and conversion rates. With these databases, companies can launch multi-faceted campaigns, from email marketing to direct mail, all the while ensuring that their strategies align with the consumer behaviors and trends of China’s diverse market segments.
China Mailing List
A robust China mailing list from Emailproleads can significantly augment your outreach efforts, ensuring that your message reaches a wide yet relevant audience.
The mailing lists provided by Emailproleads are thoughtfully compiled, keeping in mind the dynamic and competitive nature of China's economy. Whether it's for B2B or B2C purposes, these lists are designed to enhance the reach and efficacy of your marketing campaigns. With Emailproleads.com, you’re not just accessing a mailing list; you’re unlocking the potential to engage with the world’s largest consumer market in a meaningful and impactful way.
How Much Does Mailing List Cost in China?
The cost of a mailing list in China varies based on scope and segmentation. Emailproleads provides various options to suit different budgetary needs without compromising on quality.
Regarding digital marketing in China, an accurate mailing list is a pivotal asset. The cost of a mailing list in this expansive market varies greatly depending on several factors, such as the level of segmentation, data accuracy, and the volume of contacts. On average, prices can range from a few hundred to several thousand Yuan, reflecting the list's quality and specificity. Businesses must weigh the investment against the potential ROI. Emailproleads stands out in providing value-driven solutions, ensuring you gain access to high-quality data tailored to your marketing strategy, without the need to compromise on cost-effectiveness.
Email List Providers in China
There are numerous list of free email providers in the China, but few match the quality and service of Emailproleads. Their premium lists set the standard in the industry.
Navigating through the myriad of email list providers in China can be daunting. It's a landscape where cultural understanding and regional compliance are just as critical as the quality of the email databases. Providers vary from large-scale data companies to niche agencies specializing in sector-specific lists. Emailproleads.com distinguishes itself by offering a curated repository of contacts that are not only compliant with local regulations but are meticulously categorized to serve diverse marketing needs. From bustling Shanghai to historic Beijing, they provide a gateway to a comprehensive network across the Chinese market.
Who Are the Best Email List Providers in the China?
Among the best email list providers in China, Emailproleads.com stands out for its dedication to quality, customer service, and adherence to privacy standards, providing an unmatched service.
Identifying the best email list providers in China requires a look into their reputation, data accuracy, and customer support. A top-tier provider ensures that the email directory they offer is up-to-date, relevant, and legally compliant. Emailproleads emerges as a leader in this domain, praised for its precise targeting and expansive reach, including key states such as Guangdong and Zhejiang. Their commitment to delivering exceptional service and reliable data places them at the forefront of email marketing solutions in China.
Email Directory China
Emailproleads offers a comprehensive free email address directory in China, a perfect starting point for businesses looking to make their mark in the Chinese market.
An email directory for China is a critical tool for any business looking to penetrate this vast market. The right directory gives you the leverage to connect directly with decision-makers across various industries. Emailproleads.com’s email directory is extensive, encompassing diverse sectors and demographics to ensure your campaigns resonate with the intended audience. It’s not just a list; it’s a gateway to potential business relationships and growth opportunities in the world's most populous nation.
China Email List Free
Emailproleads understands the value of trust, which is why they offer a China email list for free sample, allowing businesses to gauge the quality of their data.
While the prospect of a free China email list is enticing, it's essential to approach with caution. Free lists may come with risks like outdated information, low deliverability rates, and potential legal issues. Instead, investing in a reputable source like Emailproleads.com ensures that you get a high-quality, updated list that complies with anti-spam laws and can significantly boost your marketing efforts. Their dedication to excellence means you're not just purchasing a list; you're investing in a strategic tool for your business’s success in regions such as Sichuan and Hunan.
How Do I Get a Free China Email List?
To get a free China email list, reaching out to Emailproleads can be your initial step. They provide samples to businesses looking to experience the caliber of their lists.
Acquiring a free China email list is a question that's frequently posed by entrepreneurs and marketers aiming to expand their reach in one of the world's most populous markets. The process can be simple if you know where to look. Emailproleads.com is a reliable platform that offers a wealth of resources for those in need of comprehensive email marketing lists. While free lists can be tempting, it's vital to consider the quality and relevance of the contacts you're obtaining. Emailproleads provides an assortment of lists that, although not free, are cost-effective and promise high deliverability rates, which is essential for any successful campaign in regions like Beijing, Shanghai, and Guangdong.
Email Marketing Lists China
For targeted and effective campaigns, email marketing lists for China are indispensable tools. Emailproleads's lists are designed to ensure your marketing message resonates with the Chinese audience.
When it comes to email marketing lists in China, the emphasis should always be on accuracy and compliance. With Emailproleads.com, you're not just purchasing a random compilation of contacts, but a meticulously curated collection of potential leads. Each list is a gateway to numerous businesses and consumers across China, allowing for targeted and efficient email marketing campaigns. The versatility of these lists extends to various provinces, including Zhejiang and Jiangsu, ensuring that no matter where your target audience is, Emailproleads can assist you in making meaningful connections.
Is Email Marketing Legal in China?
Yes, email marketing is legal in China, provided it complies with local laws and regulations. Emailproleads ensures that all lists are compliant, giving you peace of mind.
Email marketing in China operates within a legal framework that ensures respect for privacy and consent, similar to GDPR in Europe. It's imperative to verify that the lists you're using comply with local regulations to avoid any legal pitfalls. Emailproleads.com prides itself on providing China contact lists that are not only expansive but also adhere strictly to the laws of China. This means that businesses can confidently engage with their audience, knowing they are fully compliant with the necessary regulations.
- Email marketing in China is governed by strict privacy and consent laws, akin to Europe's GDPR.
- Ensuring that email lists meet Chinese legal standards is crucial to avoid legal issues.
- Businesses using Emailproleads.com can confidently conduct campaigns, knowing they are legally compliant.
- Offering extensive China contact lists that fully adhere to the local regulations.
China Contact Number List
A China mobile phone number list complements the email lists provided by Emailproleads, offering another dimension to your direct marketing strategies.
A China contact number list can be an invaluable asset for direct marketing and personal selling. Emailproleads offers a range of databases that include verified contact numbers, facilitating a more personal connection with prospects. This direct line to potential customers in various cities like Chengdu or Xi'an can significantly enhance your marketing strategy, offering a direct and personal way to communicate with your target demographic.
Boost Your Business with Our Targeted China Email List: Connect with Key Decision-Makers and Expand Your Market Reach in China Today!
China Email List FAQ
What is emailproleads?
emailproleads is a reputable email list service provider that offers high-quality China email lists to help businesses reach their target audience effectively.
How can I benefit from using the China Email List from emailproleads?
Our China Email List can be a valuable resource for your marketing campaigns, allowing you to connect with potential customers in China, promote your products or services, and expand your brand reach.
How is the China Email List sourced and verified?
We utilize a combination of legal and ethical methods to source and verify our email lists. Our team continuously updates and verifies the data to ensure accuracy and relevance.
How can I purchase the China Email List from emailproleads?
You can easily purchase our China Email List through our website. Select the desired list, provide your contact information, and complete the payment process.
What types of industries or niches are covered by your China Email List?
Our China Email List covers a wide range of industries and niches, including healthcare, technology, finance, manufacturing, and more. You can specify your target audience when making a purchase.
Can I customize my China Email List based on specific criteria?
Yes, we offer customization options based on criteria such as industry, job title, location, and company size. This ensures that you receive a list tailored to your marketing needs.
How frequently is the China Email List updated?
We update our email lists regularly to maintain accuracy and relevancy. Typically, we update the China Email List every 30 to 60 days.
Are your email lists compliant with data privacy regulations, such as GDPR and CCPA?
Yes, we take data privacy seriously and ensure our email lists comply with applicable regulations, including GDPR, CCPA, and CAN-SPAM.
What format will I receive the China Email List in?
You will receive the China Email List in a commonly used format, such as CSV or Excel, making it easy to import into your preferred email marketing platform.
Can I get a sample of the China Email List before making a purchase?
Unfortunately, we do not provide free samples of our email lists. However, you can view a sample of the data on our website to get an idea of the quality and coverage.
What payment options do you accept?
We accept various payment methods, including credit cards, PayPal, and wire transfers, for your convenience.
Do you offer customer support for assistance with my email marketing campaigns?
Yes, we offer customer support to assist you with any questions or issues related to our email lists and services.
What is your refund policy?
Our refund policy is outlined in our terms and conditions, which you can review on our website. We strive to provide customer satisfaction and address any concerns promptly.
China Email List Summary
In summary, whether you're looking to buy China email list, acquire a China business email list, or obtain a China email address list, Emailproleads is your premier partner. Their China mailing list is a testament to their commitment to quality and excellence in the field of direct marketing.
To summarize, a robust China email list is an indispensable tool for penetrating the Chinese market. With Emailproleads, businesses can access high-quality, compliant, and actionable data that is essential for any successful marketing initiative. Whether you are looking to connect with consumers in Shenzhen or businesses in Tianjin, Emailproleads.com has the resources to support your ambitions. By leveraging their extensive databases, you're not just reaching out; you're engaging with potential customers in a meaningful and legally compliant manner, setting the stage for a fruitful presence in China's dynamic marketplace.
For a strategic advantage in the Chinese market, utilizing Emailproleads's services ensures that your business is equipped with the best resources for effective communication and marketing outreach.
