Saudi Arabia Phone Number Database
The #1 site to find Saudi Arabia Phone Number Database and accurate B2B & B2C Phone Number Database. Emailproleads.com provides verified contact information for people in your target industry. It has never been easier to purchase an Contact list with good information that will allow you to make real connections. These databases will help you make more sales and target your audience. You can buy pre-made mailing lists or build your marketing strategy with our online list-builder tool. Find new business contacts online today!
Just $199.00 for the entire Lists

Customize your database with data segmentation
- Job Titles
- Job Function
- Company Size
- Revenue Size
- SIC Codes
- NAICS Codes
- Geographics
- Technology
- And more...

Free samples of Saudi Arabia mobile number database
We provide free samples of our ready to use Saudi Arabia contact Lists. Download the samples to verify the data before you make the purchase.

Human Verified Saudi Arabia Mobile Number Lists
The data is subject to a seven-tier verification process, including artificial intelligence, manual quality control, and an opt-in process.
Best Saudi Arabia contact number lists
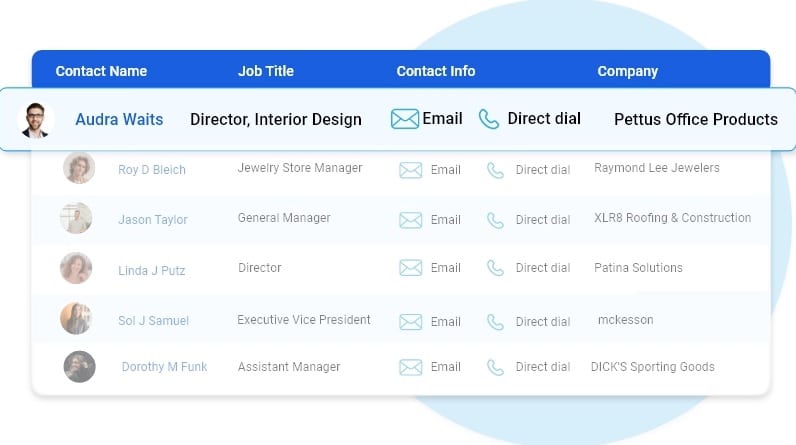
Highlights of our Saudi Arabia Contact Lists
First Name
Last Name
Phone Number
Address
City
State
County
Zip
Age
Income
Home Owner
Married
Property
Networth
Household
Cradit Rating
Dwelling Type
Political
Donor
Ethnicity
Language Spoken
Email
Latitude
Longitude
Timezone
Presence of children
Gender
DOB
Birth Date Occupation
Presence Of Credit Card
Investment Stock Securities
Investments Real Estate
Investing Finance Grouping
Investments Foreign
Investment Estimated
Residential Properties Owned
Traveler
Pets
Cats
Dogs
Health
Institution Contributor
Donates by Mail
Veteranin Household
Heavy Business
Travelers
High Tech Leader
Smoker
Mail Order Buyer
Online Purchasing Indicator
Environmental Issues Charitable Donation
International Aid Charitable Donation
Home Swimming Pool
Look at what our customers want to share





FAQ
Our email list is divided into three categories: regions, industries and job functions. Regional email can help businesses target consumers or businesses in specific areas. Saudi Arabia Email Lists broken down by industry help optimize your advertising efforts. If you’re marketing to a niche buyer, then our email lists filtered by job function can be incredibly helpful.
Ethically-sourced and robust database of over 1 Billion+ unique email addresses
Our B2B and B2C data list covers over 100+ countries including APAC and EMEA with most sought after industries including Automotive, Banking & Financial services, Manufacturing, Technology, Telecommunications.
In general, once we’ve received your request for data, it takes 24 hours to first compile your specific data and you’ll receive the data within 24 hours of your initial order.
Our data standards are extremely high. We pride ourselves on providing 97% accurate Saudi Arabia telephone number database, and we’ll provide you with replacement data for all information that doesn’t meet your standards our expectations.
We pride ourselves on providing customers with high quality data. Our Saudi Arabia Email Database and mailing lists are updated semi-annually conforming to all requirements set by the Direct Marketing Association and comply with CAN-SPAM.
Saudi Arabia cellular phone number list
Emailproleads provides Mobile Database to individuals or organizations for the sole purpose of promoting your business. In Digital Marketing. The mobile number database of Emailproleads helps to reach the highest level of business conversations.
Mobile number databases are a crucial marketing tool with many numbers from all over the globe. Since the arrival of smartphones, there has been an exponential rise in the number of buyers because technology has changed the way of marketing. Mobile number databases are essential for every retailer today in marketing and selling their goods and services. The world is now filled with mobiles that have internet connectivity across the globe.

Saudi Arabia Phone Number quality lists
Saudi Arabia contact number lists
Now and again, we can see advertisements promoting the company. These ads result in the expansion of the company. It is possible to expand your marketing further using other services for Digital Marketing like Bulk SMS, Voice Calls, WhatsApp Marketing, etc.
Emailproleads checks every mobile number in the database using various strategies and techniques to ensure that buyers receive the most appropriate and relevant customer number and successfully meet their marketing goals and objectives.
This service assists you find your loyal customers keen to purchase your product. If you’d like to see your brand acknowledged by customers, using a database of mobile numbers is among the most effective ways to accomplish this.
What is the meaning of Phone Number Data?
A telephone number is a specific number that telecommunication firms assign to their customers, thus permitting them to communicate via an upgraded method of routing destination codes. Telecom companies give whole numbers within the limits of regional or national telephone numbering plans. With more than five billion users of mobile phones around the world, phone number information is now a gold mine for government and business operations.
What is the method of collecting the phone Number Data collected?
Having the number of current and potential customers and marketing professionals opens up a wealth of opportunities for lead generation and CRM. The presence of customer numbers is an excellent way to boost marketing campaigns as it allows marketers to interact with their target audience via rich multimedia and mobile messaging. Therefore, gathering phone number information is vital to any modern-day marketing strategy. The strategies consumers can use to collect data from phone numbers include:
* Adding contact forms on websites.
* Requests to be made for phone calls from customers.
* Use mobile keyword phrases for promotions to encourage prospective customers to contact you.
* Applying app updates prompts users to change their email details each time they sign in.
* Acquiring phone numbers that are already available information from third-party service companies with the information.
What are the main characteristics of the Phone Number Data?
One of the critical advantages of phone number data is that it is created to reveal the geographic location of mobile users because phone numbers contain particular strings specific to a region or country that show the user’s precise position. This is useful in targeted campaigns, mainly where marketers target a specific area that can target their marketing efforts.
To prevent duplicates and improve accessibility, the phone number information is typically stored in the E164 international format, which defines the essential characteristics of a recorded phone number. The specifications that are followed in this format are the number code for the country (CC) and an NDC, a country code (CC), a national destination code (NDC), and the subscriber number (SN).
What do you think of the phone Number Data used for?
The possibilities that can be made possible by the phone number information are endless. The availability of a phone number database means that companies worldwide can market their products directly to prospective customers without using third-party companies.
Because phone numbers are region – and country-specific and country-specific, data from phone numbers gives marketers a comprehensive view of the scope of marketing campaigns, which helps them decide on the best areas they should focus their time and resources on. Also, governments use the data from mobile numbers to study people’s mobility, geographic subdivisions, urban planning, help with development plans, and security concerns such as KYC.
How can an individual determine the validity of Phone Number Data?
In determining the quality of the phone number information, users should be aware of the fundamental quality aspects of analysis. These are:
Completeness. All info about phone numbers within the database must be correct.
Accuracy. This measure reflects how well the data identifies the individual described within the actual world.
Consistency. This indicates how well the data provider follows the rules to facilitate data retrieval.
Accessibility. The phone number database should be accessible where the data is organized to allow easy navigation and immediate commercial use.

middle east saudi arabia email database
Saudi Phone Number Data
The Data Providers and Vendors listed in Datarade provide Phone Number Data products and examples. Most popular products for Phone Number Data and data sets available on our platform include China B2B phone number – Chinese businesses by Octobot, IPQS Phone Number Validation and Reputation through IPQualityScore (IPQS), and B2B Contact Direct Dial/Cell Phone Number Direct Dial and mobile numbers for cold calling Real-time verified contact email and Phone Number by Lead for business.
How do I get my phone Number Data?
You can find phone number data from Emailproleads.
What are data types similar that are similar to Phone Number Data?
Telephone Number Data is comparable with Address Data; Email Address Data, MAID Hashed Email Data, Identification Linkage Data, and Household-Level Identity Data. These categories of data are typically employed to aid in Identity Resolution and Data Onboarding.
Which are your most popular uses for Phone Number Data?
The top uses that involve Phone Number Data are Identity Resolution, Data Onboarding, and Direct Marketing.
Let’s say you’re running a business selling strategy that demands you to connect with the maximum number of people you can. If your job is laid off for you, it can often be challenging to determine what to do. First, you should create your list of prospective customers and then save your call data in an electronic database.
Saudi Arabia Telephone Number Lists
Though you might believe that working with lists of telephone numbers and storing them in databases is all you need to launch a cold calling campaign, it’s not the case. Since a telephone number database could contain thousands or millions of leads, along with important data points about each potential customer, It is essential to adhere to the best practices for a Database of telephone numbers. Methods to avoid becoming overwhelmed or losing important data.
To build a phone number database that delivers outcomes, you must start on the right starting point. It is possible to do this by purchasing lists of sales leads from a reliable, dependable company like ours. It’s equally important to have the right tools to allow your team to contact the most people possible.
In addition to high-quality telephone marketing lists, we provide advice on the best techniques for targeting databases and dialer software that can make lead generation more efficient and less expensive over time. Our customer service representatives are ready to assist you.
Saudi Arabia Telephone Number Database Best Practices
After you’ve established the basis for success by acquiring high-quality lead lists and implementing dialers that can boost how many calls your team receives by up to 400 percent, you’re ready to become familiar with best practices for your industry. By adhering to a list of phones and best database practices, you’ll dramatically improve the odds that your team will succeed in the short and long term.
Here are the best techniques for telemarketing databases that you should consider a priority to observe.
Get Organized
A well-organized Saudi Arabia mobile phone directory includes contacts organized according to phone country, postal, area, city, and province. By narrowing your calls to only one of the criteria, it is possible to incorporate new business information into your list, then sort and retarget top leads.
Saudi Arabia mobile number list
Create a strategy to manage your phone lists. Naturally, your organizational plan must be based on the purpose of your cold-calling campaign. Your business’s goals will affect the traits your most promising prospects have. Make a profile of the most appealing candidate based on the plans for your marketing campaign. Make sure you make your leads list to ensure that the candidates who best meet your ideal profile of a prospect are first on your list of leads. List.
Saudi Arabia cellular phone number list
Determine Who Has Access to and edit your database
Your phone number list doesn’t only represent an investment in money but also a resource that your team can use to increase sales. Although your phone number list is essential because you bought it, it’s also advantageous due to the possibility that it can improve your bottom line. In this regard, you should think carefully about who has access to and control your database.
It is generally recommended to restrict the number of users who have access to your database to only those who use it to communicate with potential customers to achieve your campaign’s goals. If an individual is not active with your marketing campaign, then there’s no reason for them to gain access to your telephone number database.
It’s also advisable to restrict access to the database you have created; it’s best to allow editing privileges to people who require them. This generally means that you only give editing rights to agents that will be conducting cold calls. It will be necessary to modify the database to make changes to records and notes that could aid in subsequent calls.
Saudi Arabia phone number database
Create Your Database
Databases are knowledge centers that store information for sales personnel. They are vital to gain knowledge and share it with your sales staff. Even if it’s just to keep call notes, callback databases can help your sales team to achieve maximum value and benefit from lists of telemarketing calls.
As time passes, your phone number list will likely expand and include more contact numbers and information on your customers. When you get recommendations from your current prospects or purchase leads lists, or either, it’s essential to grow the size of your database to include as much data as you can to assist you in achieving your goals for the business in the near and far future and at every step in between.
4. Keep Your Database
Although you want your database to expand with time, you do not want it to contain obsolete or ineffective details. To keep your database from overloading with useless information, it’s essential to maintain it regularly, including removing old records and updating your prospective customers with their contact details.
One of the most effective ways to ensure your database is to ensure that it doesn’t contain numbers listed on the Do Not Call list. If you make a call to an address that is listed on a Do Not List, you could result in your business spending lots of money, perhaps even millions. With the free tools available online, think about scrubbing all your data against the Do Not Call registry at least twice yearly.
If you’ve learned the basics of a telephone list and best practices for database management, you can contact
Saudi Arabia mobile number database
Emailproleads.com now to receive the top-quality leads lists you need within your database. Saudi Arabia phone number database free download
Today, download the mobile phone/cell numbers directory of all cities and states based on the network or operator. The database of mobile numbers is an excellent resource for advertising and bulk SMS, targeting specific regions of people, electoral campaigns, or other campaigns. Before you use these numbers, verify the ” Do Not Disturb” status in conjunction with TRAI. If it is activated, it is not permitted to use these numbers to promote your business.
Buy Saudi Arabia Phone Number Database
It’s the quickest method of building an extensive list of phone numbers for your potential customers. Pay a fixed sum (per list, contact, country, or industry) and get every mobile number you paid for and have in your possession. You can then utilize them several times to reach out to customers to convince them to purchase their products or products. Doesn’t that sound great?
Saudi Arabia phone number listing
Although it may seem like the fastest method of building a list of numbers, it’s not the case. There are a lot of risks associated with purchasing mobile marketing lists which won’t generate sales:
They’re not well-targeted. It’s impossible to be sure that every person on the bought phone lists will pay attention to the emails you’ve sent or your company worldwide.
It will help if you trust someone completely. When you purchase a mobile phone list, you’ll need to be able to trust your seller about how active the numbers are. It’s possible that the majority of the phone numbers you’re buying are not current or relevant.
Blog
Saudi Arabia Phone Number database
The reason for every view is to accomplish the following:buy Saudi Arabia Phone Number database for marketing
Logical view: The software components developed by programmers. In objects-oriented languages, these components are packages and classes. The connections between them are the relations between the classes and the packages which include inheritance, associations and dependent-on.
View of implementation — The result of the build process. This view is composed of mod-ules that represent packaged code, as well as components, which can be executed or deployable units made up of the modules. In Java the term “module” refers to an JAR file, while the term “component” is usually an WAR file, or an executable JAR file. The relationships between them comprise dependency relationships between modules as well as composition relationships between modules and components. Saudi Arabia Phone Number database free
Process view – The components running at the time. Every element is an individual process, and the relationships between them represent the interprocess communication.

Saudi Arabia Phone Number database
Deployment–How processes are mapped to machines. The elements of this model are comprised from (physical and virtual) machines as well as the processes. The interactions between machines constitute the network. This perspective also describes the relationships between machines and processes.
In addition to these view types, we also have four scenarios — the +1 in the model of 4+1– that allow views to be animated. Each scenario explains how different architectural components of each view cooperate in order to deal with the request. The logical view for example, demonstrates how the classes interact. In the same way, a scenario within the process view will show how the processes interact.
The view model 4+1 is a fantastic method to explain an application’s architecture. Each view explains an important element of the architecture and the examples show how the components of a view work together. Let’s take a look at the reasons why architecture is crucial. Saudi Arabia Phone Number database
Why is architecture important?
A program has two types of requirements. The first is the functional requirements, which specify the tasks the application is required to perform. They usually take the form of user stories. Architecture has nothing to do with deal with the functional requirements. Functional requirements can be
Saudi Arabia Phone Number business database free download implemented in almost any design including a large chunk of dirt.
Architecture is essential because it allows applications to meet the second set of requirements that is its requirements for quality of service. They are also referred to as quality attributes and are often referred to as”-ilities. The quality of the requirements for services define the runtime attributes like scalability and dependability. They also define development time features like maintainability and testability as well as deployment capability. The design you select for your application will determine the extent to which it will meet these requirements for quality. Saudi Arabia Phone Number database
A brief overview of the architectural styles Saudi Arabia Phone Number database for sale
In the real world, the architecture of a building typically follows a certain design style, like Victorian, American Craftsman, or Art Deco. The styles are a collection of design rules that restrict the design of a building’s features as well as its materials. The idea of style in architecture also applies to software. David Garlan and Mary Shaw (An Introduc-tion to Software Architecture, January 1994, able/ftp/intro_softarch/intro_softarch.pdf), pioneers in the discipline of software architecture, define an architectural style as follows:

Saudi Arabia Phone Number mailing lists
Saudi Arabia Phone Number mailing lists
A style of architecture, or architectural design describes a collection of these systems as a result of a structural arrangement. In particular the style of architecture determines the language of connectors and components that can be utilized in the context of that particular style, with a set of restrictions on how they may be used together. buy Saudi Arabia Phone Number database for marketing
A specific architectural style offers an enumeration of components (components) and connections (connectors) that you can create a visual representation of the application’s design. A typical application employs the combination of styles of architecture. For example, later in this section I describe how the monolithic architecture is an archi-tectural style that structures the implementation view as a single (executable/deploy-able) component. The microservice architecture encapsulates an application in the form of a set of loosely connected services.
The ARCHITECTURAL STYLE LAYERED
The best model of architecture is the layered structure. Layered archi-tecture arranges software components into layers. Each layer is assigned a distinct responsibility. Layered architectures also limit the relationships between layers. A layer is only dependent on either the layer beneath it (if strictly layer-ing) or one of the layers beneath it.
It is possible to apply the layering architecture for any of the 4 views mentioned earlier. The three-tier model is the layering architecture that has been that is applied to the logic view. It organizes the class of the application into the following tiers , or layers: Saudi Arabia Phone Number database
Presentation layer — Contains an application that implements the interface for users, or the external APIs
Layer of business logic – Contains the business logic
Persistence layer – Implements the logic of interfacing with the database
The layered structure is an outstanding illustration design style however it comes with important drawbacks.
Single presentation layer does not indicate the reality that an application could be likely to be used by more than one system.
One persistence layer does not represent the reality that an application is likely to be interacting with more than one database.
Saudi Arabia Phone Number business database free download

Saudi Arabia Phone Number lists
The business logic layer is defined as a dependent layer on the persistence layer. In the theory of things, this dependency blocks you from testing your process without the databases.
Additionally, the layered structure does not accurately reflect the dependencies of the well-designed application. Business logic usually defines an interface or repository of inter-faces which define the methods of accessing data. The persistence layer defines DAO classes which implement interfaces for repository. In other words, dependencies are in contrast to the layering architecture. Saudi Arabia Phone Number database
Let’s consider alternative designs that can overcome these disadvantages: the hex-agonal design. Saudi Arabia Phone Number database for sale
A BIT ABOUT HEXAGONAL ARCHITECTURE STYLE
Hexagonal architecture can be a viable alternative to the architectural style that is layered. As the figure 2.2 illustrates the hexagonal design organizes the logical views in a manner that puts the business logic in the heart of. Instead of the presentation layer the application is comprised of one or more adapters inbound that manage requests from outside by calling its business logic. Also, in lieu of a data persistence layer The application is equipped with one or more adapters outbound which are invoked by business logic and also invoke external applications. The main benefit of this design is that the logic of business does not depend on adapters. Instead, they rely on it.
Saudi Arabia Phone Number lists
The business logic is comprised of several ports. A port is a list of operations , and it’s what the logic of business interfaces with the outside world. In Java as an example the term “port” is typically described as a Java interface. There are two types of ports: outbound as well as outbound ports. Inbound ports are an API exposed by business logic that allows it to be accessed by other applications. A good illustration of an interface that is inbound would be the service that defines the public methods. Outbound ports define how the business logic calls external systems. One example of an output port would be a repository interface which is a collection of operations for accessing data. buy Saudi Arabia Phone Number database for marketing

Saudi Arabia Phone Number
The business logic is surrounded by adapters. Like ports there are two kinds of adapters: outbound and outbound. Inbound adapters handle requests from outside through the use of the inbound port. One illustration of an adapter that is inbound would be an example of a Spring MVC Controller that implements either an array of REST endpoints or the set of Web pages. Another instance is a client for a message broker that is subscribed to messages. Multiple adapters inbound can be invoked on the same port inbound.
Outbound adapters implement an outbound port that handles requests made by the business logic through invoking an external service or application. One example of an outbound adapter is an object for data access (DAO) class which performs the operations required to access a database. Another example is proxy classes that run the remote service. Outbound adapters may also be able to release events.
The main benefit of the hexagonal style is that it dissociates all business-related logic and data access and presentation logic within the adapters. The business logic isn’t dependent on the presentation logic nor the information access logic. Saudi Arabia Phone Number database
Saudi Arabia Phone Number business database free download
As a result of this decoupling it’s simpler to test business logic independently. Another advantage is that it more precisely represents the structure of modern applications. The business logic is executed by multiple adapters that each implements an API or user interface. Business logic may also be invoked by several adapters at once, every that invokes an external system. Hexagonal architecture is a fantastic way to define the structure of every service within the microservices model.
The hexagonal and layered structures are two instances of styles in architecture. Both define the basic elements of an architectural structure and places restrictions on the relationship between them. The hexagonal structure and the layered architecture with the shape of three-tier architecture, are the best way to organize the logical perspective. Let’s define the Microservice Architecture as an architecture style which organizes the view of imple-mentation.
Microservice architecture is an architectural style.
I’ve talked about the 4+1 perspective model as well as architectural styles, and I’m now able to define the mono-lithic and microservice architectural styles. Both are architectural styles. The architectural design style Monolithic Architecture encapsulates the view of implementation as a sin-gle component, one executable, (or WAR) file. The definition doesn’t mention the different views. Monolithic applications can be, for instance, having an logical view which is organized according to the principles of a hexagonal structure. Saudi Arabia Phone Number database free download
Pattern Monolithic Architecture
Structure the application as a single executable/deployable component
The microservice architecture is an architecture style. It organizes the imple-mentation view as a set of many components: executables , or WAR files. The components are services and the connectors are communications protocols that allow these services to work together. Each service is a unique logical view structure, which is usually one of hexagonal design. Figure 2.3 depicts the possible microservice architecture of an FTGO application. The services that are part of this model correspond to functional capabilities in business, like Management of orders and Restaurants. Saudi Arabia Phone Number database
Pattern: Microservice architecture Saudi Arabia Phone Number database for sale

Saudi Arabia Phone Number database
The application should be structured as a set of loosely connected, independently deployable, and independent deployable components. See
Saudi Arabia Phone Number
In this chapter, I will explain what I mean by the term “business capability . Connectors between services are created by using interprocess communication methods such as REST APIs , and Asynchronous Messaging. Chapter 3 discusses interprocess communication in more detail.
One of the main constraints of the microservice structure is the fact that services are not tightly connected. Therefore, there are limitations regarding how the services interact. To understand those limitations, I’ll try to define the term”service” explain what it means to be loosely coupled and explain why this is crucial. buy Saudi Arabia Phone Number database for marketing
What is a Service?
The term “service” refers to a stand-alone software component that is independently deployable that provides a useful function. Figure 2.4 shows the outside view of a service that in this instance will be an Order Service. An API is a service that allows its customers access to its capabilities. There are two kinds of operations: queries and commands. The API comprises commands, queries and events. A command, like createOrder() is a per-form that performs actions and changes data. A query, such as findOrderById(), retrieves data. The ser-vice can also broadcast events, like OrderCreated that are accessed by its customers. Saudi Arabia Phone Number database free download
The service’s API provides its internal implementation. Contrary to monoliths development environment, developers aren’t able create code that evades the API. This is why microservice architecture enforces the modularity of the application. Saudi Arabia Phone Number database
Each service within microservice architectures has its own structure and, in some cases, a technology stack. However, a typical service is an hexagonal structure. Its API is implemented using adapters that communicate with the business logic of the service. The operations adapter calls the logic of the business, while the events adapter releases events generated through the logic of business.
In chapter 12, where I talk about deployment technologies You’ll discover that the view of implementation for the service may take various shapes. It could be a standalone program that runs on a web platform, an OSGI bundle running inside the form of a container, or even a cloud service that is serverless. The most important condition is that the service uses an API that is independent accessible.
What is LOSE COUPLING?
An important characteristic of the microservice architecture is that the services are loosely coupled (https://en.wikipedia.org/wiki/Loose_coupling). Every interaction with a service occurs through its API that encapsulates the details of its implementation. This allows the operation of services to alter without impacting the clients of the service. Services that are loosely coupled are essential to improving the characteristics of development time, such as its maintenanceability and testability. They are easier to understand, modify and test. Saudi Arabia Phone Number database free download
Saudi Arabia Phone Number listing
The requirement that services be in loose communication and cooperate only through APIs restricts the ability of services to communicate through a database. The service’s persistent data the same way as elements of the class and make them confidential. The data’s privacy allows developers to modify the schema of their database without the need of co-coordinating with developers who are who are working on different services. Sharing data-base tables enhances the isolation of runtime. It also ensures, for instance that a service doesn’t keep database locks that hinder other services. In the future you’ll realize that one disadvantage of having databases shared is it can cause consistency in data and the ability to query between services can be more complicated. Saudi Arabia Phone Number database
The Role of Shared Libraries
Developers typically package functionality into the form of a library (module) in order that it can be used by different applications without having to write new code. In the end, where would we be today if not for Maven or NPM repositories? It is possible to utilize shared libraries within microservice architecture. It seems as a great option to reduce the amount of code duplicated within your service. However, you must ensure that you don’t introduce the coupling between your services. Saudi Arabia Phone Number database for sale
Saudi Arabia Phone Number listing
Imagine, for instance that multiple services have to modify the business object Order. One option is to bundle this functionality in a library which is utilized by several services. One thing is that using a library will eliminate the need for code duplication. However think about what happens if the requirements change in a manner that impacts the Order business object. It’s necessary to rebuild and redeploy the services. The better option is to create functions that are likely to evolve, such as order management, which is an option in a service. buy Saudi Arabia Phone Number targeted list
Try to make use of libraries to provide functions that are likely to stay the same. For instance in the typical application, it’s not sensible for any service to use a generic money class. Instead, you need to make a library utilized by the service. Saudi Arabia Phone Number database free download
The size of a service is largely irrelevant.
One issue with the term microservice is that it is the first thing you’ll encounter is the word micro. This implies that a service is tiny. This is also the case for other terms based on size, such as nanoservice or miniservice. The truth is that size isn’t a metric that is useful. Saudi Arabia Phone Number database
It is better to identify a well-designed and well-constructed service. It should be a solution that is capable of being developed by a smaller team that has a short lead time and without collaboration to other groups. In principle, a group could be responsible only for one service, and the service isn’t micro. If a service requires an enormous team or takes a lengthy time to be tested it’s likely to separate the team and the service. Also, if you have to constantly to alter a service because of changes in other services or making changes to other services, it’s an indication that it’s loosely connected. You may even have created an unidirectional monolith.
The microservice architecture conceives the application as a collection of smaller, loosely connected services. As a result, it improves the development time attributes–main-tainability, testability, deployability, and so on–and enables an organization to develop better software faster. Additionally, it increases an application’s scalability, though it’s not the primary objective. In order to create a microservice design for your application it is necessary to define the services involved and figure out the ways they interact. Let’s take a look at ways to accomplish this. Saudi Arabia Phone Number b2b database
_Saudi Arabia Phone Number leads
Definiting an application’s microservice architecture
What is the microservice architecture? Like any other software development endeavor beginning points are the requirements in writing as well as domain experts or perhaps an existing software. Much like the rest of software development, the process of defining an architecture is more of an art than a science. This article describes a simple three-step process, as illustrated in Figure 2.5 to define an application’s structure. It’s crucial to keep in mind that it’s not a procedure that you can follow in a mechanical manner. It’s likely that it will be iterative and will require lots of imagination. Saudi Arabia Phone Number database
The application is created to handle requests, therefore the first step to define its architecture is to deconstruct the requirements of the application into most important requirements. However, instead of describing requests using specific IPC technologies, such as messaging or REST I will employ the more abstract concept that of system operations. System operations are the abstraction for a request which the application is required to deal with. It’s either a request, that updates the data or a query that retrieves information. The behaviour of each command is described using an abstraction of the domain model and is further derived from specifications. Sys-tems are operations that form the architectural scenarios that show how the services work together. Saudi Arabia Phone Number address lists
Saudi Arabia Phone Number leads
The next step in this process will be to identify the process of decomposition into services. There are many options to select from. One strategy, with its roots in the field of architecture for business, is establish services that correspond to the capabilities of business. Another option is to arrange the services in domain driven design subdomains. This results in services that are structured around business concepts , not technical terms.
The third step of defining the architecture of an application is to define each service’s API. To determine this you must assign every system operation you as identified in the previous step to an application. A service could execute an operation completely on its own. Or, it could require collaboration in conjunction with different services. In this case you must decide how the service collaborates with each other, which usually requires services to facilitate additional operations. It is also necessary to choose on which IPC methods I outline in chapter 3 is the best way to create the API for each service. buy Saudi Arabia Phone Number targeted list
Saudi Arabia Phone Number Profile
There are a variety of obstacles that hinder decomposition. One of them is latency in networks. It could be that you discover that a certain decomposition will not work due to excessive round-trips between different services. Another issue with decomposition is that the synchronous communication between the services decreases their the availability of services. You may need to employ the concept of self-contained service which is which is described in chapter 3. The third challenge is the need to ensure the consistency of data across different services. It is common to need the sagas which are discussed in chapter 4. The fourth and last problem to be deconstructed is god-classes, that can be employed throughout the application. It is good to know that you can apply techniques from domain-driven design in order to remove god classes. Saudi Arabia Phone Number b2b database
This section begins by describing how to determine the application’s operation. Following that we’ll discuss methods and guidelines to break down an application into different services and then look at the challenges to decomposition, and how to overcome these. Then, I’ll outline the steps to define each API of the service. Saudi Arabia Phone Number database
Identifying system operation
The first step to define the architecture of an application is to determine the system’s operation. The initial step is to determine the requirements of the application, which includes user stories, and the related scenario for users (note that they are distinct in comparison to the architecture scenarios). The system’s functions are identified and defined by the two-step process that is illustrated in Figure 2.6. This process is inspired by the object-oriented design process covered in Craig Larman’s book Applying UML and Patterns (Prentice Hall, 2004) (see www.craiglarman.com/wiki/index.php?title=Book_Applying_UML_and_Patterns for details). The initial step creates an upper-level model of domain made up of the most important classes.
The domain model derives predominantly from the words of the user stories, while the sys-tem functions are derived mostly from verbs. You can also define the domain model with the technique known as Event Storming, which I will discuss in chapter 5. The behaviour of every system operation is explained by its impact on the domain object and their connections. System operations can create, update or remove domain objects as well as establish or alter relationships between them. Saudi Arabia Phone Number b2b database
Let’s examine how to create an upper-level domain model. Then, I’ll describe the operation of the sys-tem in relation to what is known as the domain model.
EXPANDING A HIGH-LEVELDOMAIN MODEL
The initial step in creating the system’s operations is to draw the high-level domain model of the application. It is important to note that this model is more similar to the one that will eventually be put into place. The application will not even have any single domain model as the moment you learn every service is a distinct domain model. While it’s a massive reduction of the process, a high-level domain model is useful in this phase as it establishes the language for describing the operation of the system’s operations. Saudi Arabia Phone Number address lists
Saudi Arabia Phone Number Profile
Domain models are developed with standard methods, like studying the nouns used in stories and the scenarios, and then conversing with domain experts. Take, for instance,
Definition of System Operations buy Saudi Arabia Phone Number targeted list

Saudi Arabia Phone Number business database
After you’ve created the high-level domain model it’s time to define the kinds of requests that the application has to manage. The specifics that comprise the UI are not within what is covered in this article however, you can envision that in any scenario of a user the UI will send demands to the business logic behind that will fetch and update information. FTGO is mostly web-based so the majority of requests are HTTP-based. However, it is likely that some users make use of messaging. Instead of binding themselves to a particular protocol it’s more sensible to utilize the more abstract concept that a computer operation in order to define requests. Saudi Arabia Phone Number b2c database
There are two kinds of system operation:
Commands – System operations that create data, update, or delete information Saudi Arabia Phone Number database
Queries: System procedures that can read (query) data
In the end, these system actions are correlated with REST, RPC or messaging endpoints. However, in the moment, thinking of these operations in terms of abstraction is beneficial. Let’s begin by identifying certain commands.
The best way to begin recognizing system commands is to study the verbs used in the scenarios and stories of the users. For instance, take a look at in the Place Order story. It clearly suggests that the system should offer the Create Order process. Other stories in the series connect directly to the system’s commands.
Of the two queries, findAvailableRestaurants() is probably the most architecturally significant. It’s a complicated query that involves geosearch. The geosearch component of the query consists of finding all points–restaurants–that are near a location–the delivery address. It also filters out restaurants that are not open in the event that an order has to be made and then picked up. Additionally, the speed of service is important since the query is run anytime a user would like to make an order. Saudi Arabia Phone Number database
High-level Domain Model as well as the system operations define what the application does. They are instrumental in defining the structure of the architecture of the application. The behavior of every system operation is described as a part in the framework of the domain model. Each system’s key operation represents an architecturally significant event that’s an element of the architectural description. Saudi Arabia Phone Number b2c database
When the operations of the system have been identified The subsequent step would be to determine the services of the application. As we mentioned there’s no mechanical process that you must follow. There are different decomposition methods you can employ. Each approach tackles the issue from a different angle and utilizes their own terminology. However, with all approaches the final result is the same: an architecture comprised of services focused on business, not technical terms.
The definition of services is based on to the Decompose through business capabilities pattern
One method to create microservice architecture is to separate it into the business capability. A concept derived from business architecture modeling, a capability is something an organization does to create value. The capabilities of an individual business is contingent upon the type of business. For instance those capabilities for an insurance business typically include Underwriting claims control, Billing, Compliance, and the list goes on. An online shop’s capabilities comprise the management of orders, inventory management shipping, and so on. Saudi Arabia Phone Number address lists
Pattern: Decompose based on business capabilities
Define services in relation to the capabilities of business.

Saudi Arabia Phone Number customers database
Saudi Arabia Phone Number business database
BUSINESS CAPABILITIES DETERMINE WHAT A ORGANIZATION IS ABLE TO DO
The capabilities of a business capture the nature of the business. They’re usually stable, in contrast to the way an organization manages the business it runs, and that can change with time, sometimes drastically. This is especially the case today as we see the growing technological advancements that automate a variety of business procedures. For instance it wasn’t too long ago when you could deposit the checks you had at your bank by giving them to an cashier. Then it became feasible to make checks deposit at an ATM. Nowadays, you can deposit checks with your mobile phone. As you can see, the deposit check capabilities have maintained its stability, but the way the process is carried out has changed dramatically. Saudi Arabia Phone Number b2c database
Identifying Business Capabilities buy Saudi Arabia Phone Number targeted list
The capabilities of an organization can be identified through analyzing the business’s mission, structures, and business processes. Every business capability is viewed as an service unless it’s a technical rather than business-oriented. Its specifications comprise of a range of elements, such as inputs, outputs and service-level agreements. For instance the input to an insurance underwriting capacity is the application of the consumer, and the outputs are the approval process and price. Saudi Arabia Phone Number database
The business capabilities are typically targeted at a specific business object. For instance it is Claim is the Claim company object can be described as the primary focus for an ability called the Claim managing capability. A capability can be broken down into sub-capabilities. For instance for example, the Claim management capability comes with a number of sub-capabilities, such as Claim Information Management, Claim Review, as well as Claim pay management. Saudi Arabia Phone Number customers database
It’s not hard to imagine that the commercial capabilities of FTGO comprise the following:
Supplier management
– Courier management–Managing courier information
Information management for restaurants – Managing menus for restaurants and other details such as location and opening hours
Strategies for decomposition
Information management for consumers.
The process of taking orders and completing them Saudi Arabia Phone Number database
– Order management – Allowing consumers to manage and create orders
Restaurant order management — managing the process of preparing orders in the restaurant. Saudi Arabia Phone Number customers database
– Logistics
Management of Courier availability – Managing the availability of couriers in real-time to deliver orders
– Delivery management–Delivering orders to consumers
Saudi Arabia Phone Number b2c database
Accounting
Accounting for consumer accounts – Controlling consumer billing
Accounting for restaurants – Controlling the payment to restaurants
Paying for couriers couriers
…
The top capabilities include Management of the consumer, Suppliers order taking and fulfillment as well as Accounting. There could be other top-level capabilities, which include marketing-related capabilities. The majority of top-level capabilities are broken down into sub-capabilities. For example, order taking and fulfillment is broken down into 5 sub-capabilities. Saudi Arabia Phone Number database providers
Saudi Arabia Phone Number customers database
One intriguing aspect of this structure is the presence of three related capabilities to restaurants Information management for restaurants and Restaurant order management and Accounting for restaurants. They represent three distinct aspects of the restaurant’s operations.
We’ll then look at ways you can use your abilities of business in order to design the definition of services. purchase Saudi Arabia Phone Number lists
From BUSINESS CAPABILITIES to SERVICES
After you’ve identified the company capabilities, you can then create the services for every ability or set of capabilities. Figure 2.8 illustrates the mapping from capabilities to services within services for the FTGO application. Certain capabilities at the top level such as the Accounting capability are mapped to service. In other instances sub-capabilities are linked to services. Saudi Arabia Phone Number customers database
The decision about how high in hierarchy of capability to map to services because it’s a bit subjective. My reasoning for this specific mapping can be this:
I assigned the sub-capabilities for supplier management to two different services because Couriers and restaurants are different kinds of suppliers.
I assigned the Order taking and fulfillment capabilities to three separate services, each responsible for distinct phases in the procedure. I also combined the Courier availability Management and Delivery Management capabilities and assigned the three capabilities to a single service because they’re intertwined. Saudi Arabia Phone Number database
I have mapped the Accounting feature to its own service due to the fact that the different kinds of accounting appear to be like they are.
In the future, it could be beneficial to segregate payments (of Restaurants and Couriers) and billing (of Consumers).

Saudi Arabia Phone Number b2b database
The main benefit of arranging processes around capability is, since they’re stable, the architecture is also relatively solid. The various components of the architecture might alter as the way of doing of the business evolves however the overall architecture remains the same.
However it’s crucial to remember that the features depicted in the figure 2.8 are only the initial attempt to define the structure. They will likely change as we gain more knowledge about the domain of application. Particularly, a crucial aspect of the architecture design process is examining how the services interact with each of the major architectural services. It is possible, for instance you discover that a specific decomposition is not efficient because of the high amount of interprocess communication. This means that you have to mix services. In contrast, a service could become more complex until it becomes necessary to separate it into several services. Furthermore in section 2.2.5 I will discuss several issues that could make you reconsider your choice. Saudi Arabia Phone Number business database
Let’s examine another method of decomposing the application that is built on the concept of domain-driven design. Saudi Arabia Phone Number database
Definition of services through the pattern Decompose by sub-domain
DDD as explained in the excellent book about Domain-driven design written by Eric Evans (Addison-Wesley Professional, 2003) is a strategy for creating complex software that are based on the creation of an object-oriented model for domains. Domain mode is a way of capturing the knowledge of a domain in a manner which can be used to resolve problems within the domain. It defines the terms that the team uses which is known as which is what DDD refers to as”the Ubiquitous Language. It is mirrored in the development and implementation for the app. DDD includes two fundamental concepts that are extremely helpful when using microservice architecture Subdomains and Bounded Contexts.
DDD creates a distinct modeling of each domain. Subdomains form a part of the domain which is DDD’s term used to describe the application’s problem space. Subdomains are defined by the same method used for the identification of business capabilities. You must analyze the business and determine distinct domains of knowledge. The final result is likely to include subdomains which have similarity to the capabilities of the business. The subdomains that are typical in FTGO include order taking, Order management Kitchen management, delivery, and Financials. As you can observe, these subdomains are quite similar to the business capabilities described earlier. Saudi Arabia Phone Number business database
Common CLOSURE PRINCIPLE
Another useful principle is called the common closure Principle:
The classes within a package need to be shut together to protect against the same types of changes. A change in an entire package will affect all classes within the package. Saudi Arabia Phone Number database providers
Saudi Arabia Phone Number b2c database
Robert C. Martin
The concept is this: if two classes shift in lockstep due to the same underlying reason and belong to the same category. For instance that the classes are able to implement an alternative aspect of a certain business rule. It is the goal that when the business rule is changed developers will only have to alter code in a tiny number of programs (ideally just one). Following the CCP substantially improves the ability to maintain the functionality the application. purchase Saudi Arabia Phone Number lists
It is possible to apply CCP while developing a microservice architecture, and then package components that change due to similar reasons in the same application. This reduces the amount of services that will need to be re-designed and implemented in the event of a change to a requirement. The ideal is that a change should be limited to a single team and one service. CCP is the ideal solution to the anti-pattern of distributed monoliths. Saudi Arabia Phone Number database
SRP as well as CCP are two from the eleven principles formulated in the work of Bob Martin. They’re particularly helpful when creating microservice architecture. The remaining nine principles can be utilized when creating modules and classes. For more information about SRP, CCP, and the other OOD principles, see the article “The Principles of Object Ori-ented Design” on Bob Martin’s website (http://butunclebob.com/ArticleS.UncleBob .PrinciplesOfOod).

Saudi Arabia Phone Number database free download
Decomposition based on business capability and by subdomain , along together with SRP as well as CCP are excellent methods of dissolving an application into services. To apply them effectively and develop a microservices architecture, you have to resolve some trans-action management and interprocess communication problems. Saudi Arabia Phone Number business database
The obstacles in decomposing an app services
The idea of creating a microservices architecture through the definition of ser-vices that correspond to subdomains or business capabilities appears simple. However, you may run into a few issues:
Network latency
Limited availability due to the synchronous nature of communication Saudi Arabia Phone Number database
Data consistency across all services
In order to have a consistent overview of the information
God classes preventing decomposition
LATENCY OF NETWORK
Latency in networks is an ongoing issue in distributed systems. It’s possible to find that a specific decomposition of services leads to a huge number of round-trips to two services. Sometimes, it is possible to reduce the latency down to a reasonable amount by using an API that can fetch multiple objects on a single round journey. In other cases it is better to integrate services, replacing costly IPC by using a language-specific method or Saudi Arabia Phone Number Profile functions. Saudi Arabia Phone Number database
SYNCHRONOUS INTERPROCESS COMMUNICATION REDUCES
Another issue is how create interservice connectivity in a manner that doesn’t compromise availability. For instance the most simple method for implementing the CreateOrder() procedure is to allow it to be used by the Order Service to synchronously invoke other services via REST. The disadvantage when using protocols such as REST, is it decreases accessibility of an Order Service. It won’t be able create an order if one of the other services aren’t available. Sometimes, this can be a good trade-off, however in chapter 3, you’ll discover that using asynchronous messaging that eliminates the tight cou-pling issue and enhances the availability of services, is typically the better option.
Maintaining data consistency across services
Another issue is keeping data consistency across various services. Certain system operations require update information across multiple services. For example, if restaurants accept orders that requires updates, they must happen both in The Kitchen Service and the Delivery Service. In the Kitchen Service, for example. Kitchen Service changes the status of the ticket. It also changes the status of an order. Delivery Service sched-ules delivery of the order. Both updates need to be performed in a synchronized manner. Saudi Arabia Phone Number Profile
The most common solution is to employ commit-based, two-phase trans-action management system that is distributed. However, as you’ll discover in chapter 4 of this book, this isn’t the best solution for modern-day applications. You must adopt a completely different method of managing trans-actions and which is a Saga. A saga is a series of local transactions coordi-nated with messaging. Sagas are more intricate than conventional ACID transactions, but they are able to work well in a variety of situations. One of the drawbacks of sagas they’re event-ally stable. If you have to change certain data in a synchronized fashion, it has to be part of one service, which is an obstruction to decomposing. Saudi Arabia Phone Number database providers

Saudi Arabia Phone Number business database free download
Saudi Arabia Phone Number b2b database
OBTAINING A CONSISTENT VIEW OF THE DATA
Another problem with decomposition is that it is difficult to get a truely uniform view of data across different databases. In a monolithic system the characteristics of ACID transactions ensure that queries will provide an identical overview of your database. However, in microservices even though every service’s database is con-sistent, you won’t get a uniform view of the information. If you require a consistent view of a particular data item that is stored, it should be within a single service which will prevent decompo-sition. Luckily, this is not a major issue. purchase Saudi Arabia Phone Number lists
God’s Class Prevents Decomposition
Another barrier to decomposition is that of god classes. God class are bulky classes that are utilized across an application. The god class usually implements business logic in a variety of areas of application. It usually has a huge amount of fields that are which are linked to a database table with a number of columns. The majority of applications are comprised of at the very least some of them, and each represents an idea that is central to the field such as banking accounts or e-commerce transactions and insurance policies, and the list goes on. Because god classes tie with state and behaviour for various elements of an app, it’s a huge barrier to breaking any business logic that utilizes the class into services. Saudi Arabia Phone Number Profile
This class, the Order one is an excellent example of a class that is a godclass within the FTGO application. It’s not that surprising, after all, the primary goal the purpose of FTGO is to serve meals to clients. A majority of the components of the system contain orders. In the event that FTGO application was one domain model The order class could be a vast class. It would contain state and behavior that matched various components within the program. Figure 2.10 illustrates the structure of this class which could be built by applying traditional methods of modeling. Saudi Arabia Phone Number database
As you can observe the Order class includes fields and methods related to ordering pro-cessing, restaurant order management, delivery and payment. The class also includes an intricate state model because one model is required to explain state changes from various components that make up the software. In its current state the class makes it very difficult to separate the code into services.
One option is to bundle Order class Order Class into a Library and build the central Order database. All the services that handle orders utilize this library and can access the database that is accessible. The problem with this method is that it is in violation of one of the principal principle of the microservice model and causes undesirable tight interdependence. For instance, any modification made to the Order schema will require the teams to modify the code at a time in sync.

Saudi Arabia Phone Number database free
Another approach is to put the Order database into an Order Service that is used by other services to fetch or update the order. The issue with this approach would be that this Order Service would be a data service that is based on an inadequate domain model that has very little or no business logic. None of these options are appealing, however, DDD provides a solution. Saudi Arabia Phone Number leads
An alternative is to implement DDD and make each service an individual sub-domain that has its unique domain model. This means that every one of the services within the FTGO application that is associated with orders, has its own domain model, along with its own variant of the class Order. An excellent example of the advantages of having several domain models is that of that of the Delivery Service. The way it presents an Order as depicted in Figure 2.11 is extremely straightforward such as pickup address, time of pickup delivery address, time of delivery. In addition, instead of calling it an order it is called a Delivery Service. Delivery Service utilizes the proper name, which is Delivery. Saudi Arabia Phone Number database providers
Saudi Arabia Phone Number database free download
Model of the domain model Order Service. Order Service Domain Model
The Order class in every domain model is a representation of different elements of one business entity. The FTGO application must ensure uniformity between the different objects from various services. For instance after it is established that the Order Service has authorized the consumer’s credit card, it has to create the Ticket in the Kitchen Service. In the same way, if the restaurant declines the request through The Kitchen Service, it must be canceled in the Order Service service, and the customer is credited through the service for billing. In the 4th chapter we will discuss how to keep the uniformity between the services by using the incident-driven mechanism stories. purchase Saudi Arabia Phone Number lists
In addition to posing technical difficulties In addition to posing technical challenges, having multiple domain models also impact the design of the user experience. A program must be able to translate into the users experience which is its domain model as well as the domain models of all one of its services. Within the FTGO application, for instance the status of an order displayed to the user is derived from information about the order stored across various services. This translation is typically done via an API gateway. API gateway, as discussed in the chapter 8. Despite these difficulties It is essential to determine and eliminate the god classes when defining the microservice architecture. Saudi Arabia Phone Number leads
Definition of APIs for service
As of now, we have an inventory of system operations as well as a list of possible services. Next, we need to determine the service’s API, its events and operations. An API service exists due to two main reasons: some operations relate to system functions. They are called by external clients and , possibly, through other service providers. Other operations are in place to aid collaboration between the services. These operations can only be invoked by other services. Saudi Arabia Phone Number database

Saudi Arabia Phone Number consumer database
An event is published by a service primarily in order to facilitate collaboration with other services. Chapter 4 discusses the ways in which events are utilized to create Sagas, which maintain consistency of data across different services. Chapter 7 describes the ways that events can be used to refresh CQRS view, and enable efficient querying. A program can also make use of events to alert external clients. For instance, it can utilize WebSockets to send events to a web browser.
The initial step for developing APIs for services is to assign every system function to the definition of a service. Then, we determine whether the service has to collaborate with other services in order to create an operation within the system. If collaboration is needed We then decide the APIs that other services should offer to facilitate the collaboration. We will begin by looking at the best way to assign system functions to the services. Saudi Arabia Phone Number leads
ASSIGNING SOFTWARE SYSTEM OPERATIONS
It is the first thing to choose which service will be the primary entry point for an inquiry. A lot of system functions are mapped to a specific service, however there are times when the mapping isn’t as evident. Consider, for example, the noteUpdatedLocation() operation, which updates the courier location. One way to think about it is that since it is related to couriers, this procedure must belong to the courier Service. However It’s actually that the Delivery Service that needs the courier’s address. In this instance it is best to assign the operation to a service that requires the information supplied through the process is a more appropriate option. In other scenarios it may be beneficial for an operator to be assigned to a service with the information necessary to manage it.
After assigning tasks to the services then the second step would be to choose which services will cooperate to perform every system’s operation. Saudi Arabia Phone Number database
Identifying the APIS required to SUBSTITUTE COLLABORATION ENTIRELY BETWEEN SERVICES
Certain operations on the system are entirely handled by one service. For instance when using the FTGO application Consumer Service handles the Consumer Service handles the createConsumer() procedure entirely on its own. Other system operations are spread across several services. The information required to process the request could be, for example, dispersed across several services. For instance, in order to run creatingOrder() operation Order Service Order Service must invoke the following services to confirm its preconditions and to make the post-conditions a reality: Saudi Arabia Phone Number listing
Consumer Service – Verify that the customer can make orders and get the payment details. buy Saudi Arabia Phone Number database online

marketing database Saudi Arabia Phone Number
Restaurant Service – Validate the items on the order line, confirm that the delivery address/time falls within the service area of the restaurant Check that the minimum order amount has been met and then obtain prices for the line items.
Saudi Arabia Phone Number business database free download
Kitchen Service–Create the Tickets.
Accounting Service – Authorize the customer’s credit card. Saudi Arabia Phone Number quality database
Similar to that, to enable acceptingOrder() process that in order to implement the acceptOrder() system operation, Kitchen Service must invoke the Delivery Service to schedule a courier to deliver the order. Table 2.3 illustrates the various services, their updated APIs as well as their collaborators. To define fully the APIs for services must be analyzed every aspect of the system and decide the kind of collaboration that is needed.
We’ve already identified the various services and actions that each service performs. However, it’s important to note that the structure we drawn out is extremely abstract. We’ve not chosen any particular IPC technology. Moreover, even though the term operation suggests some kind of synchronous request/response-based IPC mecha-nism, you’ll see that asynchronous messaging plays a significant role. Through this book, I discuss designs and architectural ideas that affect the way these services work.
Chapter 3 outlines particular IPC technologies, such as various synchronous communication methods, such as REST, as well as asynchronous messaging with messages broker. I explain how synchronous communication affects availability, and also introduce concepts of self-contained services that doesn’t call other services in asynchronous manner. One approach to build self-contained services is to follow CQRS. CQRS pattern, as described in chapter 7. In this chapter, the Order Service could, for instance, store a replica of the information owned of the Restaurant Service in order to reduce the need to invoke it Restaurant Service to validate an order. The Order Service keeps the replica current by signing up to the events that are published from the Restaurant Service whenever it updates its database. Saudi Arabia Phone Number listing
The logic of the API gateway collects the information required by the query by calling various services and combining their results. In this scenario the system operation is attributable an API gateway instead of an individual service. The service must implement the operations required to be performed by API gateway. API gateway. Saudi Arabia Phone Number database

buy Saudi Arabia Phone Number database
Interprocess communication within the microservice architecture
cloud-based services like cloud services, such as Twilio messaging service, and other cloud services, like the Twilio messaging system and the Stripe payments service. However, within a monolithic app such as FTGO modules, they call each other using a language-specific method or functions. FTGO developers typically don’t need be thinking about IPC in the event of working on REST API, or modules that interface into cloud service.
Contrarily, as you read in chapter 2 of this book, the microservice architecture creates applications as collection of services. They must usually work together to handle the request. Since service instances are usually processes that run on multiple machines that interact with each other, they need to use IPC. IPC plays an even larger part in a microservices architecture than in an application that is monolithic. As they transition their application to microservices Mary and the other FTGO developers will have to spend more time considering IPC. Saudi Arabia Phone Number listing
There’s plenty of IPC mechanisms to pick from. Nowadays, the most sought-after choice for REST (with JSON). It is important, however, to be aware that there is no magic bullets. It is important to carefully evaluate the alternatives. This chapter outlines a variety of IPC options, such as messaging and REST and also discusses the pros and cons of each. Saudi Arabia Phone Number database
The selection for an IPC method is an essential decision in the architecture. It has the potential to affect availability of applications. Furthermore it can affect the availability of applications. As I’ll discuss in this chapter as well as the following one, IPC even intersects with the management of transactions. I am in favor of an architecture made up of loosely coupled services that can communicate with one another via mes-saging that is synchronous. Synchronous protocols like REST are commonly used for communication with other apps. buy Saudi Arabia Phone Number database online

Saudi Arabia Phone Number id list
Saudi Arabia Phone Number database free
This chapter begins with a brief overview of interprocess communication within micro-service architecture. Then, I discuss Remote procedure invoke-based IPC and REST is the most well-known example. I discuss important subjects such as service discovery and how to deal with partial failure. Then, I explain the asynchronous messaging aspect of IPC. I also address scaling users while keeping the order of messages, properly managing duplicate messages, as well as the use of transactional messaging. In the final part, I discuss the concept of self-contained service which handle synchronous requests, but without interfacing with other services to increase availability. Saudi Arabia Phone Number quality database
A look at interprocess communication in microservices architecture
There are many different IPC technologies available to select from. Services can use synchronous request/response-based communication mechanisms, such as HTTP-based REST or gRPC. Additionally, they can utilize messages-based, asynchronous com-munication methods like AMQP or STOMP. There is also a wide range of messages formats that differ. Services can utilize human-readable text-based formats like JSON and XML. Alternately, they can make use of an efficient binary format like Avro and Protocol Buffers. Saudi Arabia Phone Number
Before I get into the intricacies of particular technology, I’d like to highlight some aspects of design that you should be thinking about. I start this section with a discussion of interaction styles, which are a technology-independent way of describing how clients and services interact. Then, I talk about the importance of clearly defining APIs within a microservice architecture, and the notion of an API-first design. Then, I address the crucial issue that is API evolution. In the final part, I go over various options for message formats and the way they determine the ease of API development. Let’s start by looking at the different styles of interaction. Saudi Arabia Phone Number database
Interaction styles
It is important to consider the type of interaction between a service’s clients and its customers prior to choosing an IPC method for the service’s API. The first thing to consider is the interaction style can help you concentrate on the main requirements and keep you from getting lost in the specifics of an IPC technology. As explained in section 3.4 The choice of interaction type affects the performance the application. In addition, as you’ll find the chapters 9, 10 and 9 it will help to select the right approach to testing integration.

buy Saudi Arabia Phone Number database online
There are many interactions between clients and service providers. As Table 3.1 illustrates the styles, they can be classified by two dimensions. The first will be whether or not the interactions are one-to-1 or one-to-many. Saudi Arabia Phone Number
One-to-one – Each client’s request is processed by a specific service.
One-to-many: Each request is handled by multiple providers.
The second aspect determines whether an interaction will be synchronous, or asynchronous: Saudi Arabia Phone Number database
Synchronous–The client is expecting a prompt reply from the server. It may even stop responding as it waits.
Asynchronous—The client does not block or even respond, if it is does not have to be immediately sent.
Table 3.1 The different interaction styles can be classified by two dimensions: one-to-1 or one-to-many as opposed to Asynchronous.
one-to-one one-to-many
Synchronous Request/response —
Asynchronous Asynchronous request/response Publish/subscribe Saudi Arabia Phone Number
One-way notifications Publish/async responses
Here are the most common kinds of one-to-one interactions:
A service user submits a request to the service, and waits for an answer. The client is expecting the response to be received quickly. It could happen to block when waiting. This is an interaction method that usually results in services being tightly linked.

Saudi Arabia Phone Number quality lists
Asynchronous request/response – A client for a service sends an inquiry to a server, which responds with asynchronous response. The client isn’t blocked when waiting because the ser-vice may not transmit the response for an extended period.
Interprocess communication within microservices architecture
One-way notification–A client of a service sends an inquiry to a service but there is no response or even sent. Saudi Arabia Phone Number database
It’s crucial to understand that the synchronous request/response style is generally in contrast with IPC technologies. Services can communicate, for instance, with another service through requests/response-style interaction using either REST or messaging. If two services communicate using messaging brokers however, the client’s service could be unable to connect until it receives an answer. This doesn’t mean that they’re in loose contact. It’s something I’ll revisit in the next chapter when discussing the effect of inter-service communications on availability. Saudi Arabia Phone Number lists
These are the various kinds of one-to many interactions:
The client may publish or send a message that is then consumed by one or more interested services.
A client can publish or async an inquiry message and waits for a specific period of time to get responses from the services of interest.

Saudi Arabia Phone Number database providers
The majority of services use an array of these interaction styles. The majority of the services that are part of the FTGO application offer both Asynchronous and Synchronous APIs for operations. Many also have events that are published. buy Saudi Arabia Phone Number database online
Saudi Arabia Phone Number consumer database
Let’s examine how to define an API of a service.
Definiting APIs within the microservices architecture
APIs or interfaces are crucial for software development. A program is made up of modules. Each module is equipped with an interface which defines the operations mod-ule’s clients may call. An interface that is well-designed exposes valuable functions while concealing the implementation. It lets the application modify without impacting the clients. Saudi Arabia Phone Number quality database
In a monolithic program the interface is usually described using a language-based program structure, such as an Java interface. An Java interface defines a set of functions that clients could use to invoke. Its implementation classes remain concealed by the application. Furthermore, since Java is a statically typed programming language and the interface is subject to change to become not compatible to the user, the program will not be able to build.
APIs and interfaces are equally crucial in a microservices architecture. The ser-vice’s API is an agreement with its customers. In chapter 2.2.1, an API of a service comprises operations, which clients are able to invoke, as well as events that are released through the services. An operation is identified with a name along with parameters and an output type. An event can be described as having a type and the set of fields. It is, as explained in section 3.3 and 3.3, sent to the message channel. Saudi Arabia Phone Number database

Saudi Arabia Phone Number address lists
The problem is that an API for a service isn’t defined by a simple code lan-guage. In essence, a service and its clients don’t have to be combined. If a new version the service is released with an API that’s not compatible it will not cause a compilation error. Instead, there’ll be problems with the runtime. Saudi Arabia Phone Number lists
Whatever IPC technique you decide to use It is essential to clearly define the API of a service using some type of interoperability definition (IDL). (IDL). Furthermore, there are solid reasons to adopt an API-first method of creating services (see http://www.api-first.org).
.programmableweb.com/news/how-to-design-great-apis-api-first-design-and-raml/how-to/ 2015/07/10 for more). You first create the interface definition. Then , you go over the definition of interface with developer of the client. After you have refined the API definition, do you launch the service. By defining the API upfront, you increase your chance of developing an API that is able to meet the requirements of its customers.
API-first design is essential
Even with small-scale projects, I’ve encountered issues because the components aren’t able to have a common API. For instance, on one project, the backend Java developer as well as the AngularJS frontend developer both claimed they had finished the development. However, the application was not working. Both the REST as well as WebSocket API that was used by the front-end software to interact with its backend was not properly specified. In the end, the two applications were unable to communicate! Saudi Arabia Phone Number lists
The specifics of API definition is dependent on the IPC method you’re employing. For instance, if you’re making use of messaging services, then the API is comprised of message channels, mes-sage types, as well as the message formats. When you’re using HTTP API, it consists of URLs, HTTP verbs, as well as the formats of the response and request. In the next chapter, I’ll discuss how to define APIs. Saudi Arabia Phone Number database
The API of a service’s API isn’t established in the ground. It is likely to change in time. Let’s examine how you can do it and think about the challenges that you’ll have to deal with. Saudi Arabia Phone Number id list

buy Saudi Arabia Phone Number database for marketing
marketing database Saudi Arabia Phone Number
APIs that are evolving
APIs will always change when new functions are introduced, old features are updated as well as (perhaps) older features are eliminated. If you’re using a monolithic app it’s easy to alter an API and to update all clients. When you’re working with a static typed programming language, the compiler can help by providing a list of errors in compilation. The main issue is the magnitude of the changes. It could take quite a while to alter a widely used API. Saudi Arabia Phone Number quality database
In a microservices-based app the process of changing an API for a service is much more difficult. Clients of a service are other services, that are typically developed by different teams. These clients could also include other software outside of the business. There is no way to make all clients upgrade at the same time as the service. Furthermore, because modern apps typically aren’t down for maintenance, it’s common to perform the upgrade in a continuous fashion for your service, which means that both the old and new versions of your service will be in operation simultaneously.
It is essential to establish strategies for dealing the challenges. The way you deal with a change to an API is dependent what you want to accomplish with the changes. Saudi Arabia Phone Number database
The Semantic Versioning specification (http://semver.org) is an excellent guide for the ver-sioning APIs. It is a set of guidelines which define how version numbers are used and incremented. Semantic versioning was originally designed to be used to manage the versioning of software, but it can also be used to version APIs in an distributed system. Saudi Arabia Phone Number mailing lists
The Semantic Versioning specification (Semvers) requires that a version number comprise three components: MAJOR.MINOR.PATCH. Each portion of a number according to the following format:
MAJOR – When you make an incompatible modification to the API
MINOR – When you make backward-compatible improvements to the API. API
PATCH–When you create a backward-compatible bug fix

buy Saudi Arabia Phone Number targeted list
There are several locations where you can utilize the version number of an API. If you’re creating REST APIs and you want to use the version number use the following method, which is explained below. utilize the most recent version as the first element in your URL’s path. If you’re developing an application that relies on messaging, you could include the version number in messages that it posts. It is important to correctly define API versions and evolve the APIs in a controlled manner. Let’s take a look at how we can deal with major and minor modifications. Saudi Arabia Phone Number mailing lists
If you only ever make these kinds of changes, older clients will work with newer services, provided that they observe the Robustness principle (https://en.wikipedia.org/wiki/ Robustness_principle), which states: “Be conservative in what you do, be liberal in what you accept from others.” Services should provide default values for missing request attributes. Clients should also ignore any additional attributes of the response. To ensure that this will be a breeze, the services and clients must employ an API for response and request that is compatible with an understanding of the Robustness principle. In this section, I’ll explain how text-based formats such JSON as well as XML generally facilitate the ability to improve APIs. Saudi Arabia Phone Number database
MAKING MAJOR, MAKING MAJOR, CHANGES Saudi Arabia Phone Number id list
Sometimes, you need to make massive changes that are not compatible with the API. Since you cannot make clients upgrade instantly an API must accommodate both versions of the API for a certain amount of time. When you’re working with an HTTP-based IPC method, like REST, one option is to include the main version number within the URL. For instance versions 1 and 2 paths are preceded by ‘/v1′ /…’, and versions 2 are preceded by ‘/v2’. /..
buy Saudi Arabia Phone Number database.’.
An alternative is to make use of HTTP’s content negotiation method to include the number of the release within the MIME type. For example, a user might make a request for the version 1.x of an Order by making the following request: Saudi Arabia Phone Number quality database
This request informs an Order Service that the client anticipates an API Version 1.x response. To be able to support several types of API adapters of the service are used to implementthe – Saudi Arabia Phone Number mailing lists

purchase Saudi Arabia Phone Number lists
The APIs will have technology that will translate between older and the new versions. As described in chapter 8of the chapter, the API gateway will most likely make use of APIs that are versioned. It might also need support for multiple versions of the API. Saudi Arabia Phone Number database
In the next section, we’ll examine the matter of message formats, the selection of which could affect the ease of developing an API can be.Saudi Arabia Phone Number id list
