ANZ Phone Number Database: Connect with ANZ Contacts Easily
The #1 site to find ANZ Phone Number Database and accurate B2B & B2C Phone Number Database. Emailproleads.com provides verified contact information for people in your target industry. It has never been easier to purchase an Contact list with good information that will allow you to make real connections. These databases will help you make more sales and target your audience. You can buy pre-made mailing lists or build your marketing strategy with our online list-builder tool. Find new business contacts online today!
Just $199.00 for the entire Lists

Customize your database with data segmentation
- Job Titles
- Job Function
- Company Size
- Revenue Size
- SIC Codes
- NAICS Codes
- Geographics
- Technology
- And more...

Free samples of ANZ mobile number database
We provide free samples of our ready to use ANZ contact Lists. Download the samples to verify the data before you make the purchase.
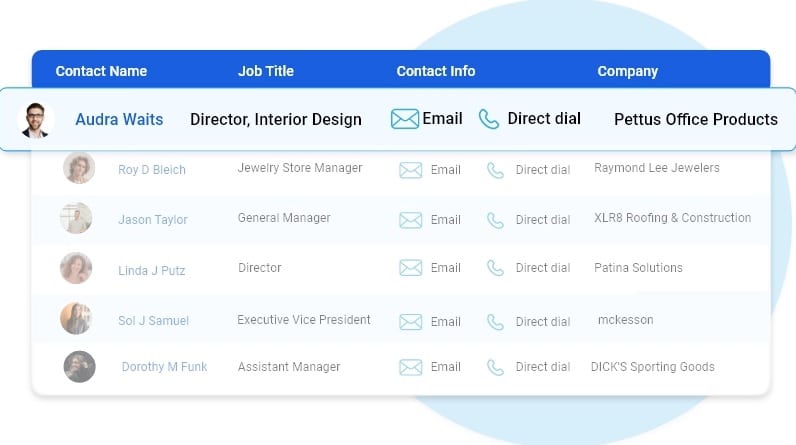

Human Verified ANZ Mobile Number Lists
The data is subject to a seven-tier verification process, including artificial intelligence, manual quality control, and an opt-in process.
Best ANZ contact number lists
Highlights of our ANZ Contact Lists
First Name
Last Name
Phone Number
Address
City
State
County
Zip
Age
Income
Home Owner
Married
Property
Networth
Household
Cradit Rating
Dwelling Type
Political
Donor
Ethnicity
Language Spoken
Email
Latitude
Longitude
Timezone
Presence of children
Gender
DOB
Birth Date Occupation
Presence Of Credit Card
Investment Stock Securities
Investments Real Estate
Investing Finance Grouping
Investments Foreign
Investment Estimated
Residential Properties Owned
Traveler
Pets
Cats
Dogs
Health
Institution Contributor
Donates by Mail
Veteranin Household
Heavy Business
Travelers
High Tech Leader
Smoker
Mail Order Buyer
Online Purchasing Indicator
Environmental Issues Charitable Donation
International Aid Charitable Donation
Home Swimming Pool
Look at what our customers want to share





FAQ
Our email list is divided into three categories: regions, industries and job functions. Regional email can help businesses target consumers or businesses in specific areas. ANZ Email Lists broken down by industry help optimize your advertising efforts. If you’re marketing to a niche buyer, then our email lists filtered by job function can be incredibly helpful.
Ethically-sourced and robust database of over 1 Billion+ unique email addresses
Our B2B and B2C data list covers over 100+ countries including APAC and EMEA with most sought after industries including Automotive, Banking & Financial services, Manufacturing, Technology, Telecommunications.
In general, once we’ve received your request for data, it takes 24 hours to first compile your specific data and you’ll receive the data within 24 hours of your initial order.
Our data standards are extremely high. We pride ourselves on providing 97% accurate ANZ telephone number database, and we’ll provide you with replacement data for all information that doesn’t meet your standards our expectations.
We pride ourselves on providing customers with high quality data. Our ANZ Email Database and mailing lists are updated semi-annually conforming to all requirements set by the Direct Marketing Association and comply with CAN-SPAM.
ANZ cellular phone number list
Emailproleads provides Mobile Database to individuals or organizations for the sole purpose of promoting your business. In Digital Marketing. The mobile number database of Emailproleads helps to reach the highest level of business conversations.
Mobile number databases are a crucial marketing tool with many numbers from all over the globe. Since the arrival of smartphones, there has been an exponential rise in the number of buyers because technology has changed the way of marketing. Mobile number databases are essential for every retailer today in marketing and selling their goods and services. The world is now filled with mobiles that have internet connectivity across the globe.

ANZ Phone Number database free
ANZ contact number lists
Now and again, we can see advertisements promoting the company. These ads result in the expansion of the company. It is possible to expand your marketing further using other services for Digital Marketing like Bulk SMS, Voice Calls, WhatsApp Marketing, etc.
Emailproleads checks every mobile number in the database using various strategies and techniques to ensure that buyers receive the most appropriate and relevant customer number and successfully meet their marketing goals and objectives.
This service assists you find your loyal customers keen to purchase your product. If you’d like to see your brand acknowledged by customers, using a database of mobile numbers is among the most effective ways to accomplish this.
What is the meaning of Phone Number Data?
A telephone number is a specific number that telecommunication firms assign to their customers, thus permitting them to communicate via an upgraded method of routing destination codes. Telecom companies give whole numbers within the limits of regional or national telephone numbering plans. With more than five billion users of mobile phones around the world, phone number information is now a gold mine for government and business operations.
What is the method of collecting the phone Number Data collected?
Having the number of current and potential customers and marketing professionals opens up a wealth of opportunities for lead generation and CRM. The presence of customer numbers is an excellent way to boost marketing campaigns as it allows marketers to interact with their target audience via rich multimedia and mobile messaging. Therefore, gathering phone number information is vital to any modern-day marketing strategy. The strategies consumers can use to collect data from phone numbers include:
* Adding contact forms on websites.
* Requests to be made for phone calls from customers.
* Use mobile keyword phrases for promotions to encourage prospective customers to contact you.
* Applying app updates prompts users to change their email details each time they sign in.
* Acquiring phone numbers that are already available information from third-party service companies with the information.
What are the main characteristics of the Phone Number Data?
One of the critical advantages of phone number data is that it is created to reveal the geographic location of mobile users because phone numbers contain particular strings specific to a region or country that show the user’s precise position. This is useful in targeted campaigns, mainly where marketers target a specific area that can target their marketing efforts.
To prevent duplicates and improve accessibility, the phone number information is typically stored in the E164 international format, which defines the essential characteristics of a recorded phone number. The specifications that are followed in this format are the number code for the country (CC) and an NDC, a country code (CC), a national destination code (NDC), and the subscriber number (SN).
What do you think of the phone Number Data used for?
The possibilities that can be made possible by the phone number information are endless. The availability of a phone number database means that companies worldwide can market their products directly to prospective customers without using third-party companies.
Because phone numbers are region – and country-specific and country-specific, data from phone numbers gives marketers a comprehensive view of the scope of marketing campaigns, which helps them decide on the best areas they should focus their time and resources on. Also, governments use the data from mobile numbers to study people’s mobility, geographic subdivisions, urban planning, help with development plans, and security concerns such as KYC.
How can an individual determine the validity of Phone Number Data?
In determining the quality of the phone number information, users should be aware of the fundamental quality aspects of analysis. These are:
Completeness. All info about phone numbers within the database must be correct.
Accuracy. This measure reflects how well the data identifies the individual described within the actual world.
Consistency. This indicates how well the data provider follows the rules to facilitate data retrieval.
Accessibility. The phone number database should be accessible where the data is organized to allow easy navigation and immediate commercial use.
Where can I purchase Phone Number Data?
The Data Providers and Vendors listed in Datarade provide Phone Number Data products and examples. Most popular products for Phone Number Data and data sets available on our platform include China B2B phone number – Chinese businesses by Octobot, IPQS Phone Number Validation and Reputation through IPQualityScore (IPQS), and B2B Contact Direct Dial/Cell Phone Number Direct Dial and mobile numbers for cold calling Real-time verified contact email and Phone Number by Lead for business.
How do I get my phone Number Data?
You can find phone number data from Emailproleads.
What are data types similar that are similar to Phone Number Data?
Telephone Number Data is comparable with Address Data; Email Address Data, MAID Hashed Email Data, Identification Linkage Data, and Household-Level Identity Data. These categories of data are typically employed to aid in Identity Resolution and Data Onboarding.
Which are your most popular uses for Phone Number Data?
The top uses that involve Phone Number Data are Identity Resolution, Data Onboarding, and Direct Marketing.
Let’s say you’re running a business selling strategy that demands you to connect with the maximum number of people you can. If your job is laid off for you, it can often be challenging to determine what to do. First, you should create your list of prospective customers and then save your call data in an electronic database.
ANZ Telephone Number Lists
Though you might believe that working with lists of telephone numbers and storing them in databases is all you need to launch a cold calling campaign, it’s not the case. Since a telephone number database could contain thousands or millions of leads, along with important data points about each potential customer, It is essential to adhere to the best practices for a Database of telephone numbers. Methods to avoid becoming overwhelmed or losing important data.
To build a phone number database that delivers outcomes, you must start on the right starting point. It is possible to do this by purchasing lists of sales leads from a reliable, dependable company like ours. It’s equally important to have the right tools to allow your team to contact the most people possible.
In addition to high-quality telephone marketing lists, we provide advice on the best techniques for targeting databases and dialer software that can make lead generation more efficient and less expensive over time. Our customer service representatives are ready to assist you.
ANZ Telephone Number Database Best Practices
After you’ve established the basis for success by acquiring high-quality lead lists and implementing dialers that can boost how many calls your team receives by up to 400 percent, you’re ready to become familiar with best practices for your industry. By adhering to a list of phones and best database practices, you’ll dramatically improve the odds that your team will succeed in the short and long term.
ANZ cell phone number list
Here are the best techniques for telemarketing databases that you should consider a priority to observe.
Get Organized
A well-organized ANZ mobile phone directory includes contacts organized according to phone country, postal, area, city, and province. By narrowing your calls to only one of the criteria, it is possible to incorporate new business information into your list, then sort and retarget top leads.
ANZ mobile number list
Create a strategy to manage your phone lists. Naturally, your organizational plan must be based on the purpose of your cold-calling campaign. Your business’s goals will affect the traits your most promising prospects have. Make a profile of the most appealing candidate based on the plans for your marketing campaign. Make sure you make your leads list to ensure that the candidates who best meet your ideal profile of a prospect are first on your list of leads. List.
ANZ cellular phone number list
Determine Who Has Access to and edit your database
Your phone number list doesn’t only represent an investment in money but also a resource that your team can use to increase sales. Although your phone number list is essential because you bought it, it’s also advantageous due to the possibility that it can improve your bottom line. In this regard, you should think carefully about who has access to and control your database.
It is generally recommended to restrict the number of users who have access to your database to only those who use it to communicate with potential customers to achieve your campaign’s goals. If an individual is not active with your marketing campaign, then there’s no reason for them to gain access to your telephone number database.
It’s also advisable to restrict access to the database you have created; it’s best to allow editing privileges to people who require them. This generally means that you only give editing rights to agents that will be conducting cold calls. It will be necessary to modify the database to make changes to records and notes that could aid in subsequent calls.
ANZ phone number database
Create Your Database
Databases are knowledge centers that store information for sales personnel. They are vital to gain knowledge and share it with your sales staff. Even if it’s just to keep call notes, callback databases can help your sales team to achieve maximum value and benefit from lists of telemarketing calls.
As time passes, your phone number list will likely expand and include more contact numbers and information on your customers. When you get recommendations from your current prospects or purchase leads lists, or either, it’s essential to grow the size of your database to include as much data as you can to assist you in achieving your goals for the business in the near and far future and at every step in between.
4. Keep Your Database
Although you want your database to expand with time, you do not want it to contain obsolete or ineffective details. To keep your database from overloading with useless information, it’s essential to maintain it regularly, including removing old records and updating your prospective customers with their contact details.
One of the most effective ways to ensure your database is to ensure that it doesn’t contain numbers listed on the Do Not Call list. If you make a call to an address that is listed on a Do Not List, you could result in your business spending lots of money, perhaps even millions. With the free tools available online, think about scrubbing all your data against the Do Not Call registry at least twice yearly.
If you’ve learned the basics of a telephone list and best practices for database management, you can contact
ANZ mobile number database
Emailproleads.com now to receive the top-quality leads lists you need within your database. ANZ phone number database free download
Today, download the mobile phone/cell numbers directory of all cities and states based on the network or operator. The database of mobile numbers is an excellent resource for advertising and bulk SMS, targeting specific regions of people, electoral campaigns, or other campaigns. Before you use these numbers, verify the ” Do Not Disturb” status in conjunction with TRAI. If it is activated, it is not permitted to use these numbers to promote your business.
Buy ANZ Phone Number Database
It’s the quickest method of building an extensive list of phone numbers for your potential customers. Pay a fixed sum (per list, contact, country, or industry) and get every mobile number you paid for and have in your possession. You can then utilize them several times to reach out to customers to convince them to purchase their products or products. Doesn’t that sound great?
ANZ phone number listing
Although it may seem like the fastest method of building a list of numbers, it’s not the case. There are a lot of risks associated with purchasing mobile marketing lists which won’t generate sales:
They’re not well-targeted. It’s impossible to be sure that every person on the bought phone lists will pay attention to the emails you’ve sent or your company worldwide.
ANZ contact number lists
It will help if you trust someone completely. When you purchase a mobile phone list, you’ll need to be able to trust your seller about how active the numbers are. It’s possible that the majority of the phone numbers you’re buying are not current or relevant.
