The #1 site to find Europe Phone Number Database and accurate B2B & B2C Phone Number Database. Emailproleads.com provides verified contact information for people in your target industry. It has never been easier to purchase an Contact list with good information that will allow you to make real connections. These databases will help you make more sales and target your audience. You can buy pre-made mailing lists or build your marketing strategy with our online list-builder tool. Find new business contacts online today!
Just $199.00 for the entire Lists

Customize your database with data segmentation
- Job Titles
- Job Function
- Company Size
- Revenue Size
- SIC Codes
- NAICS Codes
- Geographics
- Technology
- And more...

Free samples of Europe mobile number database
We provide free samples of our ready to use Europe contact Lists. Download the samples to verify the data before you make the purchase.
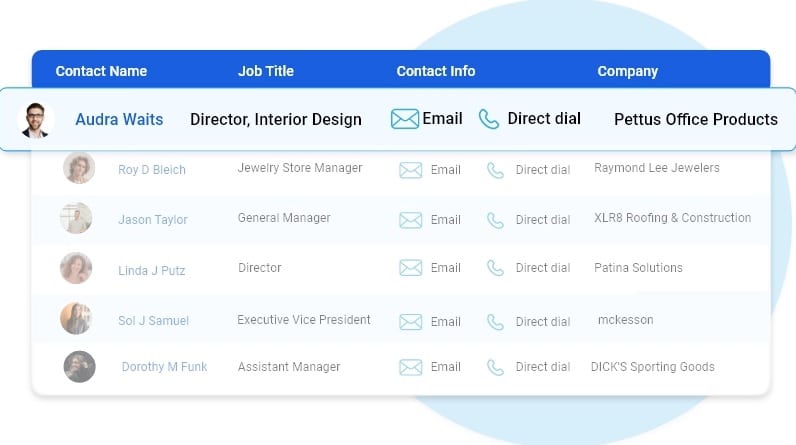

Human Verified Europe Mobile Number Lists
The data is subject to a seven-tier verification process, including artificial intelligence, manual quality control, and an opt-in process.
Best Europe contact number lists
Highlights of our Europe Contact Lists
First Name
Last Name
Phone Number
Address
City
State
County
Zip
Age
Income
Home Owner
Married
Property
Networth
Household
Cradit Rating
Dwelling Type
Political
Donor
Ethnicity
Language Spoken
Email
Latitude
Longitude
Timezone
Presence of children
Gender
DOB
Birth Date Occupation
Presence Of Credit Card
Investment Stock Securities
Investments Real Estate
Investing Finance Grouping
Investments Foreign
Investment Estimated
Residential Properties Owned
Traveler
Pets
Cats
Dogs
Health
Institution Contributor
Donates by Mail
Veteranin Household
Heavy Business
Travelers
High Tech Leader
Smoker
Mail Order Buyer
Online Purchasing Indicator
Environmental Issues Charitable Donation
International Aid Charitable Donation
Home Swimming Pool
Look at what our customers want to share





FAQ
Our email list is divided into three categories: regions, industries and job functions. Regional email can help businesses target consumers or businesses in specific areas. Europe Email Lists broken down by industry help optimize your advertising efforts. If you’re marketing to a niche buyer, then our email lists filtered by job function can be incredibly helpful.
Ethically-sourced and robust database of over 1 Billion+ unique email addresses
Our B2B and B2C data list covers over 100+ countries including APAC and EMEA with most sought after industries including Automotive, Banking & Financial services, Manufacturing, Technology, Telecommunications.
In general, once we’ve received your request for data, it takes 24 hours to first compile your specific data and you’ll receive the data within 24 hours of your initial order.
Our data standards are extremely high. We pride ourselves on providing 97% accurate Europe telephone number database, and we’ll provide you with replacement data for all information that doesn’t meet your standards our expectations.
We pride ourselves on providing customers with high quality data. Our Europe Email Database and mailing lists are updated semi-annually conforming to all requirements set by the Direct Marketing Association and comply with CAN-SPAM.
Europe cellular phone number list
Emailproleads provides Mobile Database to individuals or organizations for the sole purpose of promoting your business. In Digital Marketing. The mobile number database of Emailproleads helps to reach the highest level of business conversations.
Mobile number databases are a crucial marketing tool with many numbers from all over the globe. Since the arrival of smartphones, there has been an exponential rise in the number of buyers because technology has changed the way of marketing. Mobile number databases are essential for every retailer today in marketing and selling their goods and services. The world is now filled with mobiles that have internet connectivity across the globe.
Europe contact number lists
Now and again, we can see advertisements promoting the company. These ads result in the expansion of the company. It is possible to expand your marketing further using other services for Digital Marketing like Bulk SMS, Voice Calls, WhatsApp Marketing, etc.

Europe Phone Number id list
Emailproleads checks every mobile number in the database using various strategies and techniques to ensure that buyers receive the most appropriate and relevant customer number and successfully meet their marketing goals and objectives.
This service assists you find your loyal customers keen to purchase your product. If you’d like to see your brand acknowledged by customers, using a database of mobile numbers is among the most effective ways to accomplish this.
What is the meaning of Phone Number Data?
A telephone number is a specific number that telecommunication firms assign to their customers, thus permitting them to communicate via an upgraded method of routing destination codes. Telecom companies give whole numbers within the limits of regional or national telephone numbering plans. With more than five billion users of mobile phones around the world, phone number information is now a gold mine for government and business operations.
What is the method of collecting the phone Number Data collected?
Having the number of current and potential customers and marketing professionals opens up a wealth of opportunities for lead generation and CRM. The presence of customer numbers is an excellent way to boost marketing campaigns as it allows marketers to interact with their target audience via rich multimedia and mobile messaging. Therefore, gathering phone number information is vital to any modern-day marketing strategy. The strategies consumers can use to collect data from phone numbers include:
* Adding contact forms on websites.
* Requests to be made for phone calls from customers.
* Use mobile keyword phrases for promotions to encourage prospective customers to contact you.
* Applying app updates prompts users to change their email details each time they sign in.
* Acquiring phone numbers that are already available information from third-party service companies with the information.
What are the main characteristics of the Phone Number Data?
One of the critical advantages of phone number data is that it is created to reveal the geographic location of mobile users because phone numbers contain particular strings specific to a region or country that show the user’s precise position. This is useful in targeted campaigns, mainly where marketers target a specific area that can target their marketing efforts.
To prevent duplicates and improve accessibility, the phone number information is typically stored in the E164 international format, which defines the essential characteristics of a recorded phone number. The specifications that are followed in this format are the number code for the country (CC) and an NDC, a country code (CC), a national destination code (NDC), and the subscriber number (SN).
What do you think of the phone Number Data used for?
The possibilities that can be made possible by the phone number information are endless. The availability of a phone number database means that companies worldwide can market their products directly to prospective customers without using third-party companies.
Because phone numbers are region – and country-specific and country-specific, data from phone numbers gives marketers a comprehensive view of the scope of marketing campaigns, which helps them decide on the best areas they should focus their time and resources on. Also, governments use the data from mobile numbers to study people’s mobility, geographic subdivisions, urban planning, help with development plans, and security concerns such as KYC.
How can an individual determine the validity of Phone Number Data?
In determining the quality of the phone number information, users should be aware of the fundamental quality aspects of analysis. These are:
Completeness. All info about phone numbers within the database must be correct.
Accuracy. This measure reflects how well the data identifies the individual described within the actual world.
Consistency. This indicates how well the data provider follows the rules to facilitate data retrieval.
Accessibility. The phone number database should be accessible where the data is organized to allow easy navigation and immediate commercial use.
Where can I purchase Phone Number Data?
The Data Providers and Vendors listed in Datarade provide Phone Number Data products and examples. Most popular products for Phone Number Data and data sets available on our platform include China B2B phone number – Chinese businesses by Octobot, IPQS Phone Number Validation and Reputation through IPQualityScore (IPQS), and B2B Contact Direct Dial/Cell Phone Number Direct Dial and mobile numbers for cold calling Real-time verified contact email and Phone Number by Lead for business.
How do I get my phone Number Data?
You can find phone number data from Emailproleads.
What are data types similar that are similar to Phone Number Data?
Telephone Number Data is comparable with Address Data; Email Address Data, MAID Hashed Email Data, Identification Linkage Data, and Household-Level Identity Data. These categories of data are typically employed to aid in Identity Resolution and Data Onboarding.
Which are your most popular uses for Phone Number Data?
The top uses that involve Phone Number Data are Identity Resolution, Data Onboarding, and Direct Marketing.
Let’s say you’re running a business selling strategy that demands you to connect with the maximum number of people you can. If your job is laid off for you, it can often be challenging to determine what to do. First, you should create your list of prospective customers and then save your call data in an electronic database.
Europe Telephone Number Lists
Though you might believe that working with lists of telephone numbers and storing them in databases is all you need to launch a cold calling campaign, it’s not the case. Since a telephone number database could contain thousands or millions of leads, along with important data points about each potential customer, It is essential to adhere to the best practices for a Database of telephone numbers. Methods to avoid becoming overwhelmed or losing important data.

Europe Phone Number database free
To build a phone number database that delivers outcomes, you must start on the right starting point. It is possible to do this by purchasing lists of sales leads from a reliable, dependable company like ours. It’s equally important to have the right tools to allow your team to contact the most people possible.
In addition to high-quality telephone marketing lists, we provide advice on the best techniques for targeting databases and dialer software that can make lead generation more efficient and less expensive over time. Our customer service representatives are ready to assist you.
Europe Telephone Number Database Best Practices
After you’ve established the basis for success by acquiring high-quality lead lists and implementing dialers that can boost how many calls your team receives by up to 400 percent, you’re ready to become familiar with best practices for your industry. By adhering to a list of phones and best database practices, you’ll dramatically improve the odds that your team will succeed in the short and long term.
Europe cell phone number list
Here are the best techniques for telemarketing databases that you should consider a priority to observe.
Get Organized
A well-organized Europe mobile phone directory includes contacts organized according to phone country, postal, area, city, and province. By narrowing your calls to only one of the criteria, it is possible to incorporate new business information into your list, then sort and retarget top leads.
Europe mobile number list
Create a strategy to manage your phone lists. Naturally, your organizational plan must be based on the purpose of your cold-calling campaign. Your business’s goals will affect the traits your most promising prospects have. Make a profile of the most appealing candidate based on the plans for your marketing campaign. Make sure you make your leads list to ensure that the candidates who best meet your ideal profile of a prospect are first on your list of leads. List.
Europe cellular phone number list
Determine Who Has Access to and edit your database
Your phone number list doesn’t only represent an investment in money but also a resource that your team can use to increase sales. Although your phone number list is essential because you bought it, it’s also advantageous due to the possibility that it can improve your bottom line. In this regard, you should think carefully about who has access to and control your database.
It is generally recommended to restrict the number of users who have access to your database to only those who use it to communicate with potential customers to achieve your campaign’s goals. If an individual is not active with your marketing campaign, then there’s no reason for them to gain access to your telephone number database.
It’s also advisable to restrict access to the database you have created; it’s best to allow editing privileges to people who require them. This generally means that you only give editing rights to agents that will be conducting cold calls. It will be necessary to modify the database to make changes to records and notes that could aid in subsequent calls.
Europe phone number database
Create Your Database
Databases are knowledge centers that store information for sales personnel. They are vital to gain knowledge and share it with your sales staff. Even if it’s just to keep call notes, callback databases can help your sales team to achieve maximum value and benefit from lists of telemarketing calls.
As time passes, your phone number list will likely expand and include more contact numbers and information on your customers. When you get recommendations from your current prospects or purchase leads lists, or either, it’s essential to grow the size of your database to include as much data as you can to assist you in achieving your goals for the business in the near and far future and at every step in between.
4. Keep Your Database
Although you want your database to expand with time, you do not want it to contain obsolete or ineffective details. To keep your database from overloading with useless information, it’s essential to maintain it regularly, including removing old records and updating your prospective customers with their contact details.
One of the most effective ways to ensure your database is to ensure that it doesn’t contain numbers listed on the Do Not Call list. If you make a call to an address that is listed on a Do Not List, you could result in your business spending lots of money, perhaps even millions. With the free tools available online, think about scrubbing all your data against the Do Not Call registry at least twice yearly.
If you’ve learned the basics of a telephone list and best practices for database management, you can contact
Europe mobile number database
Emailproleads.com now to receive the top-quality leads lists you need within your database. Europe phone number database free download
Today, download the mobile phone/cell numbers directory of all cities and states based on the network or operator. The database of mobile numbers is an excellent resource for advertising and bulk SMS, targeting specific regions of people, electoral campaigns, or other campaigns. Before you use these numbers, verify the ” Do Not Disturb” status in conjunction with TRAI. If it is activated, it is not permitted to use these numbers to promote your business.
Buy Europe Phone Number Database
It’s the quickest method of building an extensive list of phone numbers for your potential customers. Pay a fixed sum (per list, contact, country, or industry) and get every mobile number you paid for and have in your possession. You can then utilize them several times to reach out to customers to convince them to purchase their products or products. Doesn’t that sound great?
Europe phone number listing
Although it may seem like the fastest method of building a list of numbers, it’s not the case. There are a lot of risks associated with purchasing mobile marketing lists which won’t generate sales:
They’re not well-targeted. It’s impossible to be sure that every person on the bought phone lists will pay attention to the emails you’ve sent or your company worldwide.
Europe contact number lists
It will help if you trust someone completely. When you purchase a mobile phone list, you’ll need to be able to trust your seller about how active the numbers are. It’s possible that the majority of the phone numbers you’re buying are not current or relevant.
Blog
Europe Phone Number database
Mary along with her colleagues from FTGO are close to finishing the first part of their service. While it’s not fully developed, it’s being run on developer laptops as well as using the Jenkins CI server. It’s still not enough. Software is not of significance for FTGO until it’s in production and is accessible to users. FTGO has to put their software into production. buy Europe Phone Number database
Deployment is the combination of two concepts that are interconnected which are architecture and process. The process of deployment consists of the steps that need to be completed by the peopleoperating and developers – to put software in production. The deployment-ment architecture is the design of the environment in which the software operates. Both the aspects of deployment have been drastically altered since the time I started developing Enterprise Java applications in the late 1990s. The process of manually dropping code on the wall to be pushed into production has now become largely automated. As Figure 12.1 illustrates the physical production environment has been replaced with a lighter and mobile computing infrastructure. Europe Phone Number database
In the 1990s when you were looking to introduce an application to production, the initial step was to drop your application, along with instructions for operation across the room to operations. For instance, you could create an issue ticket with operations asking them to launch the application. Everything that happened afterwards was the responsibility of the operations team, in the event that they encounter problems that they required assistance to solve. A bit of a twang, operations bought and installed heavy and expensive applications servers like WebLogic and WebSphere. They would then log in to the console of the application server and install your software. They will take care of these machines as if they were their pets installing patches and upgrading the software. Europe Phone Number customers database

Europe Phone Number database
In the late 2000s, expensive application servers were replaced by open-source web containers that were lightweight, like Apache Tomcat and Jetty. It was possible to run multiple applications within the web containers, but only one application per web container became possible. Additionally, virtual machines began replacing physical devices.
However, machines were considered pets to be loved by all, and their deployment was an manual fundamen-tally process.
The deployment process today is completely different. Instead of delegating the production code to a separate team, the implementation of DevOps implies developers are accountable for the deployment of their app or service. In certain organizations operations provide developers with an interface for deploying their code. Perhaps, even more importantly when the tests are passed the deployment pipeline automatically puts the code into production. Europe Phone Number database
The computing resources that are used in production environments have also been transformed radical-ly as physical machines are removed. Virtual machines running on extremely automated cloud like AWS are replacing the long-lived, pet-like physical as well as virtual machines. The modern-day virtual machines are unchangeable. They are treated as disposable animals instead of animals and are destroyed and rebuilt rather than modified. Containers, a lightweight abstraction layer that sits on the virtual machine are becoming a popular method of deploying applications. There is also an even lighter servers-less platform for deployment, like AWS Lambda for a variety of scenarios.
It’s not a coincidence that the development of deployment methodologies and structures has been in line with the increasing use of the microservices architecture. A single application could have hundreds or even tens of different applications written in a range of frames-works and languages. Since every service is a tiny application, you could are running tens or hundreds applications that are in production. It’s no longer possible to, for instance, allow administrators to manually set up the servers or services. If you’re looking to scale up microservices and require a fully automated deployment procedure and infrastructure.Europe Phone Number customers database
Figure 12.2 illustrates a high-level overview of an environment for production. The production environment allows developers to set up and manage their services, and the deployment pipeline is used to release new versions of the services as well as users to gain access to features that are incorporated by these services. Europe Phone Number database
A production environment should implement four essential capabilities:
Service management interface allows developers to develop or update services. The ideal interface would be an REST API that is invoked by command-line or GUI software for deployment.
Runtime service management – Attempts to ensure that the desired amount of instances of the service are operating in all times. In the event that a particular service fails to function or is unable to respond to requests it is required that the production environment restart it. If a machine is damaged and the production environment fails to recover, it must restart the service instances on an alternative machine. Europe Phone Number customers database
Monitoring provides developers with an understanding of the performance of their services such as log files and other metrics. If there is a problem the production environment must notify the developers. Chapter 11 outlines monitoring, sometimes referred to as observation.
Request routing – Routes requests made by users to the service. Europe Phone Number database

Europe Phone Number mailing lists
Implementing services in language-specific packages, for example WAR files or Java JAR. It is worth exploring this option since even though I’d suggest using any of the alternatives however, the drawbacks of this option are what motivate alternatives.
The deployment of the services in virtual machine that makes deployment simpler by packing the service into the virtual machine image to can be used to encapsulate the technology stack of the service.
The deployment of services as containers that are lighter as virtual machine. I will show you how to install this FTGO app’s Restaurant Service using Kubernetes, an extremely well-known Docker orchestration platform. email marketing database Europe Phone Number
Europe Phone Number mailing lists
The deployment of services via serverless deployment that is even more contemporary than containers. We’ll discuss how to implement Restaurant Service using AWS Lambda which is a well-known serverless platform. buy Europe Phone Number database
Let’s begin by looking at ways to use services in language-specific packages.
Implementing services using the Language-specific packaging pattern for format Europe Phone Number customers database
Imagine that you wish to install this FTGO Application’s Restaurant Service, which is an Spring Boot-based Java application. One approach to deploy this service is making use of the service as a specific language package pattern. In this case it is the case that what’s being used in production and controlled by the runtime of the service is a specific service that is part of its own language-specific package. For Restaurant Service, that’s either the executable JAR file or an WAR file. Other languages for instance NodeJS the term “service” refers to an archive of sources and modules. For certain languages, like GoLang the term “service” refers to an executable that is specific to the operating system. Europe Phone Number database
Pattern: Specific packaging format for languages
Implement a language-specific program into production. See http://microservices.io/ patterns/deployment/language-specific-packaging.html.
To install Restaurant Service on a machine it is necessary to install the required runtime and in this case, it is JDK. If it’s a WAR formatted file then you’ll need to install a web-based container like Apache Tomcat. After you’ve set up the machine, copy the file to the machine and begin the service. Every service instance is run as an JVM process. Europe Phone Number customers database
Ideally, you’ve configured your deployment pipeline to automately move the service from production, as illustrated in Figure 12.3. The deployment pipeline creates the executable JAR file or WAR file. Then, it calls the production environment’s management interface to launch the new version.
In production, each instance is in fact a JVM running on a system with the JDK as well as JRE installed. Europe Phone Number database
The term “service instance” refers to generally an individual process but could be a collection of processes. The Java service instance is, for instance, an application running the JVM. A NodeJS service may create multiple worker processes to handle requests concurrently. Certain languages allow multiple service instances in this process.

Europe Phone Number lists
Sometimes , you may set up a single instance of service on a single machine, while you have the option of deploying multiple instances of the service within the exact machine. In this case, as the figure 12.4 illustrates, you can run several JVMs on one machine. Each JVM is running one service instance.
Virtual or physical machines
The separation between them. Europe Phone Number database
This technique is often used to deploy applications on traditional heavyweight and expensive server platforms, such as WebLogic or WebSphere. You can also bundle services into OSGI bundles, and then run several instances of service within each OSGI container. Europe Phone Number Profile
It is true that the Service as a specific language-specific program pattern comes with both advantages and negatives. Let’s begin by looking at the advantages.
The benefits from the service as a specific language pattern for a package
A Service that is a specific language pattern comes with a number of advantages:
Fast deployment
Utilization of resources efficiently, especially in the event of running several instances simultaneously on the computer or within the same process.
Let’s take a look at each.
EXPRESS DEPLOYMENT
One of the major advantages of this design is that the process of deploying a service instance is quite fast. You copy the service onto an appropriate host and then start it. When the application is created in Java then you copy an JAR (or WAR) file. In other languages, like NodeJS or Ruby You copy your source code. In any case the number of bytes copied across the network is extremely tiny. Europe Phone Number database
Additionally, the process of starting an application is not always lengthy. If the service runs as an independent process, you can start it. If the service is among several instances running within this same process you can either dynamically deploy it into the container , or reboot the containers. Due to the absence of overhead, the process of starting a service typically takes just a few minutes. Europe Phone Number Profile
EFFICIENT UTILIZATION OF RESOURCES
Another advantage of this model is that it utilizes resources effectively. Multiple service instances are able to share the same machine and the operating system. It’s also more efficient in the event that multiple instances of service are running within the same. For instance, multiple web applications can be running on one Apache Tomcat server and JVM.
The drawbacks of Service as a language-specific package pattern Service as a specific language-specific program design Europe Phone Number database

Europe Phone Number
Despite its attractiveness however, Service as a specific language-specific package pattern comes with a number of significant disadvantages:
The lack of encapsulation for the stack of technology. email marketing database Europe Phone Number
Europe Phone Number lists
There is no way to limit the amount of resources used by an instance of a service.
Absence of isolation while running several service instances simultaneously on the same computer. buy Europe Phone Number database
Automatically determining the best place to put service instances can be a difficult task.
Let’s take a look at each drawback.
INCAPSULATION of the STACK TECHNOLOGY
The operations team needs to know the exact details on how to deploy each service. Every service requires a specific edition of runtime. For instance, a Java website application, as an instance requires specific version of Apache Tomcat and the JDK. Operation must install the appropriate version of every required software program. Europe Phone Number database
For added complexity the services are written in various frames and languages. They could be written in different versions of these languages as well as frame-works. Thus, the team responsible for development has to share a lot of information with operations. This can increase the likelihood of making mistakes in deployment. For instance, use an incorrect version of runtime for the language. Europe Phone Number Profile
A DISABILITY TO CONSTRAIN RESURES ACCESSED BY A SERVICE INSTANCE
Another issue is that you cannot limit the amount of resources used by the service instance. A service instance could use up the entire memory or CPU, thereby depriving other instances of service and operating systems. It could occur, for instance caused by a bug.
INVALIDATION WHILE running multiple service instances on the same machine Europe Phone Number database
The issue becomes even more severe when multiple instances are running in the exact same computer. In the absence of isolation, it results in a malfunctioning service instance may cause problems for other service instances. In the end, the application could be unreliable particularly when running multiple instances of a service on the same machine. Europe Phone Number listing
Automatically determining where to place INSTANTS FOR SERVICE IS A CRASH
Another problem when running multiple service instances within the same computer is the best place to put service instances. Each machine is equipped with a specific number of resources like memory, CPU, and so on. Moreover, every service instance requires a certain number of resource. It is crucial to assign instances of service to the machines in a manner which makes use of the machines efficiently without overburdening them with too much. As I’ll explain in a moment the VM-based cloud and container orchestration frameworks manage this task automatically. If you’re deploying natively it’s likely that you’ll have to decide on the best location.
As you can observe, despite its popularity it is not without its limitations. Service as a specific language-specific programming pattern is not without its drawbacks. This is a very infrequent technique, unless efficiency is more important than other considerations. Europe Phone Number database

Europe Phone Number listing
Let’s take a look at some modern ways to deploy solutions that eliminate these issues.
The Service can be deployed as a virtual machine model
Again, imagine that you’re planning to implement your FTGO Restaurant service, however, this time, it’s on AWS EC2. Another option is to create and set up an EC2 instance and then transfer on it an executable file or WAR. While you may gain some benefits from the cloud, this method is not without its drawbacks, as mentioned in the section on pre-ceding. An alternative, and more modern method is to bundle the service in an Ama-zon Machine Image (AMI) as illustrated in the figure 12.6. The service instances are an EC2 instance that was created using the AMI. The EC2 instances are typically handled via one of the AWS Auto Scaling group, which tries to ensure that the desired amount of healthy instances are continuously running.
The pattern is to deploy an application as a virtual machine Europe Phone Number listing Europe Phone Number database
A virtual machine is constructed by the deployment pipeline of the service. The pipeline for deployment as the figure 12.6 illustrates, uses the VM image builder that creates an VM image that includes the code of the service and any software is needed for it to function. For instance it is this VM builder for the FTGO application installs JDK as well as the service’s executable JAR. It is the VM image builder will configure to the VM imaging machine so that it runs the program whenever the VM is booted, using the init system of Linux like upstart.
There are many instruments that deployment pipelines could make use of to build VM images. One early tool for creating EC2 AMIs is Aminator, created by Netflix, which used it to deploy its video-streaming service on AWS (https://github.com/Netflix/ aminator). An updated VM image creator is Packer that, unlike Aminator offers a wide range of virtualization techniques that include EC2, Digital Ocean, Virtual Box and VMware (www.packer.io). For Packer to build an AMI create an AMI, you must create a config-uration document that defines the base image as well as a set of providers that install software and set up the AMI. Europe Phone Number listing
About Elastic Beanstalk
Elastic Beanstalk which is offered by AWS It’s a straightforward method to deploy your service by using VMs. Upload your code like a WAR file and Elastic Beanstalk deploys it as one or more load-balanced, managed EC2 instances. Elastic Beanstalk may not be so popular than, for instance, Kubernetes, but it’s an easy method of deploying microservices-based applications on EC2. Europe Phone Number database
In a unique way, Elastic Beanstalk combines elements of the three deployment patterns discussed within this section. It supports a variety of packaging formats for a variety of languages that include Java, Ruby, and .NET. It runs the application using VMs instead of creating an AMI the application uses the base image to install the application at the initial startup.
Elastic Beanstalk can also deploy Docker containers. Every EC2 instance is running a col-lection comprising one or several containers. Contrary to the Docker orchestration framework which will be discussed further in this chapter the scaler will be the EC2 instance, not containers. email marketing database Europe Phone Number
Europe Phone Number
Let’s take a look at the advantages and drawbacks of this method.
The advantages of using services as virtual machines

email phone number
A Service that is a pattern for a virtual machine provides a range of advantages: buy Europe Phone Number database
The VM image is a representation of everything that technology has to offer.
Service instances that are isolated.
Utilizes a mature cloud infrastructure.
Let’s examine each one.
The VM Image CAPSULATES THE STACK OF TECHNOLOGY
One of the advantages of this method can be that the VM image is a complete representation of the service along with all its dependencies. This eliminates the need to properly install and configure the software that the service needs to function. After a service is packaged as a virtual machine it is an uninspiring black box which encapsulates your service’s technology stack. The VM image is able to be used anyplace, without modifications. The API to deploy the service is now an API for managing the VM administration API. The deployment process becomes simpler and robust. Europe Phone Number lists
Service INSTANCES ARE ISOLATED
A significant benefit to virtual machines is every service is run in total iso-lation. That, in the end is among the major objectives of the technology behind virtual machines. Virtual machines have an arbitrary amount of memory and CPU and is unable to use resources that are available to other services. Europe Phone Number database
USES MATURE CLOUD INFRASTRUCTURE
Another advantage of running these microservices on virtual machines is they are able to leverage a mature, highly controlled cloud infrastructure. Clouds that are public like AWS try to plan VMs physically on machines in such a manner that doesn’t overload the machine. They also offer valuable options like load balancing for traffic across the VMs as well as autoscaling. Europe Phone Number lists
The disadvantages of using services as VMs
This Service pattern as a VM pattern comes with a few negatives:
Less-efficient resource utilization
Slow deployments
Overhead for system administration
Let’s take each drawback one by one. Europe Phone Number database
LESS-EFFICIENT RESERVE Utilization
Every service instance is subject to the burden of a complete virtual machine, which includes it’s operating system. Additionally, a common open IaaS virtual machine comes with only a small number of VM sizes, which means that the VM is likely to be used in a limited way. This won’t be an issue for Java-based services since they’re quite heavy. This could be a poor method of deploying light NodeJS as well as GoLang services. Europe Phone Number lists
RELATIVELY SLOW DEPLOYMENTS
The process of creating the VM image usually takes a amount of time due to its size. VM. There are many bits that must be moved across the network. Also, creating an VM from an VM image can take a lot of time due to, yet again, the volume of data that needs to be transferred over the network. The operating system running within the VM will take some time to start although it is an actual word. The process, which may takes a couple of minutes, is more efficient than the conventional deployment method. However, it’s a lot slower than the lighter deployment methods you’ll learn about in the near future. Europe Phone Number database
SYSTEM ADMINISTRATION OVERHEAD
It is your responsibility to patch the operation system and running time. The administration of systems may seem to be inevitable when you deploy software, but later on in section 12.5 I’ll discuss the serverless deployment method, which removes this type of system administration. Europe Phone Number mailing lists

Europe Phone Number Profile
Let’s take a consider a different way to implement microservices that’s light in weight, yet has many of the advantages that virtual machine applications offer.
Implementing services with the help of the Service the container pattern
Containers are a advanced and light deployment method. They’re an operating-system-level virtualization mechanism. A container as shown in the figure 12.7 shows, is typically one, but occasionally multiple processes that are running within the sandbox. This separates them from the other container. A container that runs the Java services, for instance is typically comprised in one or more of the JVM process.
From the point of view of a program running within containers, it’s being on its own computer. It usually uses its own address which means it doesn’t have port conflicts. All Java processes for instance listen to port 8080. Each container is equipped with its own filesystem root. The runtime for containers utilizes operating system functions to differentiate the containers from one another. The most famous instance of a runtime for containers is Docker but there are other options like Solaris Zones. Europe Phone Number mailing lists
Once you have created a container you can define the CPU, memory resources and, depending on the implementation of the container maybe I/O resources. The run-time of the container regulates these restrictions and prevents containers from taking over the machine’s resources. If you’re using the Docker orchestration framework like Kubernetes is crucial to identify the resources of the container. The reason is that the orchestration framework relies on the resources requested by a container to determine the appropriate device that will run the container, and thus make sure that the machines aren’t overwhelmed.Europe Phone Number database
Figure 12.8 illustrates the process of the deployment of a service in an image in a container. When the service is built the deployment pipeline employs an image-building program for containers that reads the code of the service along with an explanation of the image. It then create the image of the container and save it to an image registry. When it is time to run, the image is extracted from the registry, and used to build containers.
Let’s examine the runtime and build-time steps in greater in depth. Europe Phone Number mailing lists
The deployment of services with Docker
For a service to be deployed as containerized, you have to pack it in the container image. Container images are filesystem image that consists of the application as well as any software needed in order to operate the program. It’s typically an entire Linux base filesystem but smaller images can also be employed. To deploy, for instance, the Spring Boot-based service you’ll need to create a container that contains the executable JAR and the appropriate version of JDK. Similar to deploying an Java web-based application, you create a container image comprising the WAR file Apache Tomcat, and the JDK. Europe Phone Number consumer database

Europe Phone Number customers database
Europe Phone Number database
CONSTRUCTING A DOCKER IMAGE BUILT
The first step to build an image is creating the Dockerfile. A Dockerfile provides the steps to create an Docker containers image. It defines the basic container image, the instructions to install software and configure the container, as well as the shell command that runs after the container is built. Listing 12.1 illustrates the Dockerfile that was which is used to build the image needed to be used by the Restaurant Service. It creates a container image that contains the executable JAR file. It sets the container up to execute the java -jar the command on start-up. buy Europe Phone Number database
SENDING A DOCKER IMAGE OVER A REGISTRY
The last step in the building process is to upload the newly created Docker image onto what’s called an registry. A registry for Docker is the equivalent to the Java Maven repository for Java libraries as well as an NodeJS NPM registry that is used for NodeJS packages. Docker Hub is an example of an open Docker registry that is comparable with Maven Central or NpmJS.org. However, for your specific applications, you’ll most likely want to make use of private registry offered by service providers, like Docker Cloud Registry as well as AWS EC2 Container Registry. Europe Phone Number quality lists
There are two Docker commands in order to push an image into the registry. First, you must use Docker Tag, which gives the image a name preceded by hostname. Europe Phone Number database
The container’s name is the same as the name.
It is run as an in-background daemon
Binds port 8080 on the container with port 8082 on the host machine.
Implementing services by through the service as an example of a container pattern 397
and an optional port of and optional port of. The image’s name can also be prefixed with the version number of the registry, which is crucial when you create new releases of the service. For instance, if the hostname for this registry was registry.acme.com then you’d utilize this command to label the image:
docker tag ftgo-restaurant-service registry.acme.com/ftgo-restaurant-service:1.0.0.RELEASE
After that, you can utilize the docker push function to upload the image into the registry Europe Phone Number quality lists
docker push registry.acme.com/ftgo-restaurant-service:1.0.0.RELEASE
The command usually takes shorter time than you think. This is because an image created with Docker image comes with what’s called a layered file system that allows Docker to only transfer a small portion of the image across the network. The operating system of the image, Java run-time, and the application itself are all separate layers. Docker is only required to transfer the layers that do not already exist within the source. Therefore, the process of the transfer of an image across an internet-connected network is very fast in the sense that Docker only needs to transfer the layers of the application that comprise a tiny portion that make up the picture. Europe Phone Number database

Europe Phone Number b2c database
After we’ve moved the image into an appropriate registry, let’s take a explore how to make an image container.
RUNNING A DOCKER CONTAINER
After packaging your service in an image for a container and you’re ready to create at least one container. This container framework will then pull the registry image onto an production server. It will create one or more containers from the image. Each container represents an example of the service you offer. Europe Phone Number quality lists
Like you’d imagine, Docker provides a docker run command that starts and then starts the container. Listing 12.3 illustrates how to make use of this command to start the Restaurant Service. Docker Run can be used with many arguments, which include the image of the container and the specification of the environment variables that should be set in the runtime containers. These are used to send an externalized configuration like the database’s network location, and many more.
The docker run command is able to pull an image out of the registry, if needed. It then creates and begins the container. It then runs the java -jar command that is specified within the Dockerfile. Europe Phone Number database
The docker run command might seem straightforward but there are a few problems. One of them is that docker run isn’t a reliable method to set up a service since it creates a container that runs on a single computer. The Docker engine comes with basic management capabilities like automatic restarting of containers in the event that they fail or the machine is restarted. However, it isn’t able to handle crash-related issues.
Another issue is that they generally don’t exist on their own. They are dependent to other providers, like messaging brokers and databases. It would be beneficial to deploy or deploy an entire system and all its dependents in a single. Europe Phone Number quality lists
An alternative that is particularly beneficial for development is to utilize Docker Compose. Docker Compose is an application that allows you to specify a list of contain-ers with the YAML file. You can then begin and end the containers in a group. Additionally it is the YAML file can be used as a method to define a variety of externally configura-tion properties. For more information about Docker Compose I suggest taking a look at Docker in Action from Jeff Nickoloff (Manning, 2016) and examining the docker-compose.yml file included in the demonstration code.
The issue of Docker Compose, though, is that it’s only available on one machine. For reliable deployment of services it is necessary to use an Docker orchestration framework like Kubernetes which transforms an entire set of machines into a resource pool. I’ll explain how you can use Kubernetes later within section 12.4. Let’s first review the advantages and drawbacks that come with using containers. Europe Phone Number consumer database
Europe Phone Number listing
The benefits of using services as containers
Containers for services have numerous advantages. First, containers offer a lot advantages over virtual machines:
The technology stack is encapsulated where the API for managing your service is transformed into your container API.

Europe Phone Number b2b database
Service instances are not isolated. Europe Phone Number id list
The resources of Service instances are limited.
However, unlike virtual machines containers are a light technology. Container images are generally quick to construct. For instance, on my laptop, it can take just five seconds to create an Spring Boot application as a container image. Transferring a container image across the network, for instance moving it to or from the registry of the container is also fairly quick, due to the fact that only a fraction of an image’s layers needs to move. Containers can also begin fast, as there’s no long OS boot procedure. When a container is launched the only thing that is running is the service.
There are disadvantages to deploying services in containers Europe Phone Number quality lists
A major drawback to containers is that you are responsible for the heavy lifting that is undifferentiated of managing the images in the container. You have to patch the operating software and the running time. In addition except for a cloud-hosted container solution like Google Container Engine or AWS ECS, you need to manage the container’s infrastructure, and perhaps the VM infrastructure that it is running on. purchase Europe Phone Number lists
Implementing the FTGO application using Kubernetes
After having looked at containers and their advantages let’s examine how to set up an application called the FTGO Application’s Restaurant Service using Kubernetes. Docker Compose, which is described in section 12.3.1 It is a great tool for testing and development. However, to run reliable containers-based services in production, you’ll require a more sophisticated runtime for con-tainers, like Kubernetes. Kubernetes is an Docker orchestration framework, which is a layer of software built on the top of Docker which turns a number of machines into a resource pool for running services. It strives to ensure that the required number of instances for every service operating continuously even when service instances or machines go down. The flexibility of containers with the power of Kubernetes is an effective method of deploying services. Europe Phone Number database
In this article I begin by providing an introduction to Kubernetes and its capabilities, and its architecture. Then, I will show how to set up a service with Kubernetes. Kubernetes is a complicated topic and a comprehensive coverage is beyond the subject of this book. Hence, I’ll only explain how to utilize Kubernetes from the viewpoint of an engineer. For more information I suggest Kubernetes In Action, written from Marko Luksa (Manning 2018, 2018).
A brief overview of Kubernetes purchase Europe Phone Number lists
Kubernetes is an Docker orchestration framework. It is a Docker orchestration framework considers an entire set of machines operating Docker as an array of resources. You can instruct the Docker orchestration framework how to launch N instance of your application and it will take care of the remainder. Figure 12.9 illustrates the structure of an orchestration framework for Docker. Docker orchestration framework. Europe Phone Number database
An orchestration platform for Docker, for example Kubernetes is a framework that serves three primary purposes:
Resource management– Treats a group of machines as an array of memory, CPU as well as storage volume, transforming the group of machines into one machine.
Scheduling–Selects the device to operate your application. In default, scheduling takes into account the needs of the container as well as each node’s resource requirements. It can also use affinity, which places containers on the same node and anti-affinity, which puts containers on various nodes.
Service management–Implements the concept of named and versioned services that map directly to services in the microservice architecture. The orchestration framework guarantees that the required number of healthy instances are running throughout the day. It balances the load of requests across these instances. Orchestration framework makes periodic upgrades to services, and allows you to return to an older version. purchase Europe Phone Number lists
Frameworks for orchestrating Docker are a growing method to make it easier to deploy apps. Docker Swarm is part of the Docker engine, making it simple to configure and utilize. Kuber-netes is more difficult to manage and set up yet it’s more advanced. As of the writing time, Kubernetes has tremendous momentum and a huge open community of open source. Let’s have a study of the way it operates. Europe Phone Number consumer database
Europe Phone Number leads
KUBERNETES ARCHITECTURE
Kubernetes is run by the basis of a cluster of computers. Figure 12.10 illustrates the structure of the Kubernetes cluster. Every machine in the Kubernetes cluster can be categorized as a master, or a node. A typical cluster has few masters, perhaps just one, and numerous nodes. The master machine is responsible for the management of the cluster. The node acts as a working machine which has at least one pod. It is the Kubernetes’ primary unit of deployment. It is the containers. Europe Phone Number id list
Europe Phone Number database free download
A master oversees several parts that include:
API server — The API server is a REST API to deploy and manage services, which is used by the kubectl command line interface, for instance.
Etcd is a Key-Value NoSQL database that stores cluster’s data. purchase Europe Phone Number lists
This deployment definition allows Kubernetes to call Restaurant Service’s health-check endpoint. As explained in chapter 11, a health-check endpoint allows Kubernetes to assess the state of the service. Kubernetes implements two tests. The first one is called readinessProbe. It makes use of to determine if it should redirect traffic to a particular service instance. In this case, Kubernetes invokes the /actuator/health HTTP endpoint each 20 seconds following an initial 30 second delay giving it the chance to begin initializing. If a certain (default is 1) (default to 1) of readinessProbes that are repeated succeed, Kubernetes considers the service to be ready. However, when a certain number (default three) of successive readinessProbes do not succeed, the service is considered in a position to declare it ready. Kubernetes will only send traffic to the instance in the event that the readinessProbe shows it is prepared. buy Europe Phone Number targeted list
The second health check is called the livenessProbe. It’s set up the same way like the readyProbe. However, instead of determining whether traffic is routed to a particular service for instance, it is able to determine the possibility that Kubernetes should shut down and begin a new service. If a certain number (default 3, default) of liveness-Probes failing in consecutive sequence Kubernetes will cease operations then restart service.
Once you’ve completed an YAML file, you are able to make or edit the deployment applying the Kubectl application command:
kubectl apply -f ftgo-restaurant-service/src/deployment/kubernetes/ftgo-restaurant-service.yml
This command sends an inquiry at Kubernetes API server. Kubernetes API server that results in the creation of the deployment as well as the pods.
To set up this deployment it is necessary to first create the Kubernetes secret, which is ftgo-db-secret. A quick and secure method to create this deployment is to follow these steps: Europe Phone Number database
kubectl create secret generic ftgo-db-secret \
–from-literal=username=mysqluser –from-literal=password=mysqlpw
This command generates a secret which contains username and password for the account as well as password that is specified in the command line. Learn more about Kubernetes in the documentation (https://kubernetes buy Europe Phone Number targeted list
.io/docs/concepts/configuration/secret/#creating-your-own-secrets) for more secure ways to create secrets. Europe Phone Number database
CREATING A KUBERNETES SERVICE
The pods are up and running as is it is expected that the Kubernetes deployment will do its best keep them functioning. The issue is that the pods are assigned dynamically IP addresses. As so, they’re not that helpful to clients who want to send the HTTP request. In chapter 3.3, the best solution is to employ an automated service discovery system. buy Europe Phone Number targeted list

Europe Phone Number database free
Another approach is to employ the client-side discovery method and set up an appropriate service registry, like Netflix OSS Eureka. However, it is possible to get around this by making use of the service discovery feature that is built into Kubernetes and also define what is a Kubernetes service.
Service is Kubernetes-based object that gives the users from one pod or several with a reliable endpoint. It is a service with an IP address as well as an DNS number that resolves the IP address. The service is able to balance traffic according to the IP address across all the pods. Listing 12.5 provides the Kubernetes service that is used for Restaurant Service. This service routes traffic from http://ftgo-restaurant-service:8080 to the pods defined by the deploy-ment shown in the listing.
Installing the API gateway
This Kubernetes services used for Restaurant Service, shown in the listing 12.5 is accessible only via the cluster. This isn’t a problem for Restaurant Service, but what is the deal with API Gateway? Its job is to direct traffic from outside towards the application. This means it needs to be accessible to anyone outside of the cluster. Luckily, a Kubernetes service can be used in this for this scenario too. The service we discussed earlier was an ClusterIP service that is the default. However, there are two different kinds of services: NodePort and LoadBalancer. Europe Phone Number consumer database
Europe Phone Number Profile
An NodePort service is accessible through the cluster-wide port that is accessible across all nodes within the cluster. All traffic through that port from any node in the cluster is distributed on the pods in backend. It is necessary to select a port that falls within the 30000-32767 range. For instance, the list 12.6 is a service which directs users to the port 30000 from Consumer Service. Europe Phone Number id list
It is the YAML definition of the NodePort service that connects traffic to ports
8082 in Consumer Service
apiVersion: v1 Europe Phone Number database
type of service
metadata:
name: ftgo-api-gateway spec: buy Europe Phone Number targeted list
Type: NodePort
ports:
nodePort: 30000 port: 80
targetPort: 8080
selector:
app: ftgo-api-gateway
—
The type of a product is specified.
of NodePort
The cluster
wide port
API Gateway is within the cluster using the URL http://ftgo-api-gateway and out-side the URL http:// 3000/, where node-ip address refers to the address on the Internet of one node. After setting up a NodePort service, you are able to create, for instance, an AWS Elastic load balancer (ELB) to balance load requests coming from the internet across all the nodes. One of the advantages of this strategy is that it allows the ELB is completely in your control. You are completely in control when setting it up. buy Europe Phone Number database for marketing
An NodePort kind of service doesn’t have to be your only option. It is also possible to use the Load-Balancer Service that automatically sets up an Cloud-specific load balancer. The load balancer is an ELB in the event that Kubernetes operates on AWS. One benefit of this kind of solution is the fact that it means you do not have to manage the load balancer yourself. The downside is that, even though Kubernetes offers a handful of options to configure the ELB including for the SSL certifiability, it means that you will have little control over the configuration. Europe Phone Number database
Zero-downtime deployments
Imagine you’ve made some changes to Restaurant Service and want to introduce those changes into production. Updates to a running service are straightforward in three steps with Kubernetes:

Europe Phone Number consumer database
Create a new image for the container and upload it into the registry with the same method described earlier. The only difference is that the image will be tagged with a dif-ferent version tag–for example, ftgo-restaurant-service:1.1.0.RELEASE.
Modify the YAML file that is used by the deployment of the service so it is referencing the latest image.
Update the deployment with the Kubectl apply-f command. buy Europe Phone Number database for marketing
Kubernetes will then carry out an upgrade process that rolls out to the pods. It will create pods incrementally with version 1.1.0.RELEASE and then shut down the pods running version 1.1.0.RELEASE.
1.0.0.RELEASE. What’s amazing about how Kubernetes accomplishes such a thing is the fact that it won’t block old pods until the successors are ready to take on requests. It makes use of its readinessProbe mechanism, which is a health check mechanism, as described earlier in this chapter to determine if the pod is ready. This means that there always will be pods to take care of requests. In the end, assuming that the new pods are able to start that is, all pods in the deployment will be running the latest version. Europe Phone Number database
But what happens if there’s an issue and the 1.1.0.RELEASE pods aren’t starting? Maybe there’s a glitch, for instance, a wrong spelling of the container name or a misplaced environment variable to define a new configuration property. If the pods don’t begin, the deployment will be stuck. In this case you’ll have two choices. One option is to correct the YAML file, and then run the kubectl application -f command to make the update. Another alternative is to reverse the deployment. Europe Phone Number database free
Europe Phone Number business database
A deployment is a record of rollouts, also known as rollouts. Every time you update your deployment, it is created the rollout again. This means that you are able to return a deployment to an earlier version by running this command Europe Phone Number id list
kubectl rollout undo deployment ftgo-restaurant-service
Kubernetes will then replace pods that are running version 1.1.0.RELEASE with the pods running older version 1.0.0.RELEASE.
The Kubernetes deployment is an excellent method to run services without interruption. What happens if a problem is discovered only after the server is fully operational and is receiving production traffic? In this case, Kubernetes will continue to release new versions, which means an increasing number of users could be affected. While your monitoring system can likely detect the issue quickly and reverse your deployment can’t be able to avoid affecting at the very least a few users. To resolve this issue and to make the process of rolling out the latest edition of your service stable it is necessary to distinguish deployment, which involves having the service in production, from the release of the service, which is making it accessible to handle production traffic. Let’s take a look at ways to achieve this using a mesh for service. buy Europe Phone Number database for marketing
Utilizing a mesh service to distinguish release from deployment
The usual method to roll out the latest version of an application is to first test it in an environment that is staged. Once it passes the test in the staging environment, it’s time to launch it in production using an upgrade rolling process that replaces older instances of the service with brand new instances of the service. One thing is that, as you’ve just seen, Kubernetes deployments make doing rolling upgrades very simple. However this method assumes that once a version of a service has completed the tests on the test environment it can be used in production. Unfortunately, this isn’t always the scenario. buy Europe Phone Number database for marketing

Europe Phone Number database free download
One reason is that staging isn’t likely to be a perfect clone and if there is no reason than the production system will likely to be larger and capable of handling a lot more traffic. It’s also a time-consuming task to keep both environments in sync. Due to the discrepancies there is a chance that bugs will only be discovered in the production. Even if it was an exact copy of the original it’s not a assure that testing will find all bugs. Europe Phone Number database
The most reliable method to release a new version is to distinguish the release from its deployment.
Running during the production environment
The release of a service and making it available to the end-users
Then, you can deploy the service into production by using the steps below:
Introduce the new version to production, without forwarding any requests to it.
Try it out in production.
Let it be available to a select amount of users.
In the future, it will be released to a growing amount of customers until the system is handling all production traffic. Europe Phone Number database for sale
If there’s an issue, you can revert to the previous version. Otherwise when you’re sure that the new version is functioning properly, remove the previous version. Europe Phone Number database
In the ideal scenario, these procedures will be carried out through an automated deployment pipeline that examines the newly installed service for any errors.
Traditionally, segregating deployments and releases this manner has proven to be difficult since it takes a lot of effort to set it up. One of the benefits of using a mesh is that this type of deployment makes it significantly simpler. The term “service mesh” refers to as discussed in chapter 11, networking infrastructure which manages all communication between the service and other applications and services. Apart from taking on certain responsibilities associated with microservice chassis frameworks the service mesh also offers load balancing based on rules and routing that allows you to safely operate multiple versions of your service simultaneously. In this section, you’ll be able to see how you can direct test users to a specific version of the service, and users to a different one for instance. Europe Phone Number database
In chapter 11, as I’ve described There are many service meshes that you can choose from. In this article I’ll demonstrate how to use Istio popular, an open-source service mesh created through Google, IBM, and Lyft. I start by giving an review of Istio and some of its numerous options. Then, I explain how to create an application using Istio. Following that, I demonstrate how to make use of its traffic-routing capabilities to launch and then release an upgrade for an existing service. Europe Phone Number database for sale

email marketing database Europe Phone Number
OVERVIEW OF THE ISTIO SERVICE MESH
The Istio website defines Istio as “An open platform that allows you to connect to, manage as well as secure your microservices” (https://istio.io). It’s a layer of networking that allows all your service’s network traffic is routed. Istio offers a wide array of features arranged into four major categories:
Traffic management includes service discovery, load balance, routing rules, and circuit breakers
Security — Secures interservice communication by through Transport Layer Security (TLS) Europe Phone Number database free
Telemetry — Captures metrics about the network’s traffic, and then implements distributed tracking Europe Phone Number database free
Europe Phone Number customers database
Policy enforcement–Enforces quotas and rate limits
This section is focused on Istio’s ability to manage traffic. Europe Phone Number id list
Figure 12.11 illustrates the Istio’s design. It is comprised in a control plane as well as the data plane. The control plane performs management functions, such as making the data plane configurable to direct traffic. The data plane is comprised of Envoy proxy servers, one per ser-vice.
The two major elements of the control plane include the Pilot and Mixer. The Pilot collects information about the services deployed from the infrastructure. When it runs on Kubernetes for instance the Pilot collects the healthy pods and services. It then configures the Envoy proxy to direct traffic according to defined routing rules. The Mixer receives telemetry data from the Envoy proxies , and implements policies.
Istio Envoy proxy Istio Envoy proxy is a modified version of Envoy (www.envoyproxy.io). It’s a powerful proxy that is compatible with a variety of protocols that include TCP and low-level protocols like HTTP and HTTPS as well as higher-level protocols. It also supports MongoDB, Redis, and DynamoDB protocols. Envoy also allows for solid interservice communication by incorporating features like circuit breakers, limiters on rate and automatic Retries. It allows secure communication within the application using TLS to ensure inter-Envoy communications. Europe Phone Number database
Istio utilizes Envoy as sidecars, an application or container that is run alongside Istio’s service instances and addresses cross-cutting issues. When it runs on Kubernetes it is the Envoy proxy acts as an instance of the pod of the service. Other environments which do not use the pod concept, Envoy is in the same container with the service. All traffic coming and going from the service goes through the Envoy proxy which routes the traffic in accordance with the routing rules that are given to it by its control plane. For instance direct Service Service communication becomes Service Source Envoy Destination Envoy Service. Europe Phone Number database for sale

buy Europe Phone Number database
Pattern: Sidecar
Implement cross-cutting concerns within containers or sidecar processes which runs alongside that service. See http://microservices.io/patterns/deployment/sidecar.html.
Istio is configured with Kubernetes style YAML file configuration. It also has a command line tool known as istioctl which is similar to Kubectl. It is used by istioctl to create, update and deleting rules and policies. If you are working with Istio on Kubernetes you are able to make use of Kubectl.
Let’s examine how to create a service using Istio.
ESTIO – A SERVICE DEPLOYED ISTIO
Deploying a service using Istio is quite simple. You need to define an Istio Kubernetes Service and a Deployment for each of your applications services. Listing 12.7 gives the definition of Service as well as Deployment in relation to Consumer Service. Although it’s pretty similar to the definitions that I provided earlier however, there are some variations. It’s because Istio is a bit more specific in its specifications for Kubernetes’ pods and services: Europe Phone Number database for sale
An Kubernetes service port has to utilize the Istio name convention. [- [where protocol is http,, grpc mongo or redis. If the port is not named, Istio will treat the port as a TCP port, and will not use rules-based routing.
A pod should have an app label such as app: ftgo-consumer-service, which identifies the service, in order to support Istio distributed tracing.
In order to run multiple versions of a service simultaneously, the name of a Kubernetes deployment must include the version, such as ftgo-consumer-service-v1, ftgo-consumer-service-v2, and so on. The pods of a deployment should bear an indication of the version like the version number: V1, that identifies the version to ensure that Istio can direct traffic to an exact very Europe Phone Number address lists
If you’re reading this, you might be thinking of how you can start the Envoy proxy in the pod that hosts the service. Luckily, Istio makes that remarkably simple by automating the modification of the pod’s definition in order to add Envoy as an Envoy proxy. There are two methods to accomplish this. The first option is to utilize the manual sidecar injection method and then run the command isioctl-kube-inject: Europe Phone Number database
istioctl kube-inject -f ftgo-consumer-service/src/deployment/kubernetes/ftgo-consumer-service.yml | kubectl apply -f –
This command opens an YAML file in Kubernetes and outputs the modified configuration which contains an Envoy proxy. The changed configuration is piped into the kubectl application. Europe Phone Number business database free download
Europe Phone Number b2c database
Another way to connect an Envoy Sidecar into the pod would be to make use of an automatic sidecar injec-tion. If this feature is activated the service is deployed with kubectl application. Kubernetes automatically calls Istio to change the definition of the pod in order to add it with the Envoy proxy.
SUBMIT ROUTING RULES to the V1 VERSION buy Europe Phone Number database online

Europe Phone Number id list
Let’s imagine that you deployed the ftgo-consumer-service-v2 deployment. Without the routing rule, Istio load balances requests across all versions of the service. It would, therefore, load balance across versions 1 and 2 of ftgo-consumer-service, which defeats the purpose of using Istio. To ensure that you are able to release an updated version, you have to create the routing rules that route each and every request to latest version. Europe Phone Number address lists
It is composed from two Istio objects which are an VirtualService and an DestinationRule.
It is responsible for routing all requests to the v1 subset of pods that comprise Consumer Service. In later posts, I present more complicated examples of how to route in accordance with HTTP requests and load balance across several weighted destinations.
Alongside VirtualService it is also necessary to define the DestinationRule that specifies some or all subsets of pods to be used in the purpose of defining a service. Subsets of pods is usually an instance of a service version. A DestinationRule could also establish traffic policy, for example, loading-balancing algorithms. This is what’s the DestinationRule for Consumer Service.
This deployment is called ftgo-consumer-service-v2. It names its pods using the version of v2. After creating this deployment, both versions of the ftgo-consumer-service will be running. However, due to rule of routing, Istio will not route traffic to version 2. Now, you’re ready to connect some test traffic to version 2. Europe Phone Number database
When you’re confident that the service is able to cope with production, you are able to increment the amount of traffic flowing to the pods in version 2 until it is at 100 percent. After that, Istio isn’t routing any traffic to the pods in version 1. You can let them run for a while before deleting the version 1. deployment. Europe Phone Number address lists
In allowing you to segregate deployment and release, Istio makes rolling out the latest version of the service more secure. But I’ve only scratched the possibilities of Istio’s capabilities. At the date of this article the latest version of Istio currently is 0.8. I’m eager to see Istio and other meshes for service evolve and become an integral element in a production.
Implementing services with servers using Serverless deployment pattern
The language-specific packaging (section 12.1) The Service as a virtual machine (section 12.2) along with Service as a Container (section 12.3) Patterns are quite distinct however they do share certain common features. First, with all three of them, you have to preprovision some computing resources, either virtual machines, physical containers, or machines. Certain deployment platforms use autoscaling that dynamically alters the amount of virtual machines or containers in accordance with the amount of load. You’ll still be required to purchase VMs or containers even when they’re not in use. Europe Phone Number address lists
Another characteristic that is commonplace is that you’re accountable for the system administration. If you’re operating any type of device, you need to modify the Operating System. If you’re running physically-based machines, that involves stacking and racking. Additionally, you are responsible for managing the runtime for the language. This is an illustration of what Ama-zon refers to as “undifferentiated the heavy lifting.” In the beginning days of computers system administration, it’s been among the things that you must do. In the end however, there’s an alternative solution for serverless.

buy Europe Phone Number database online
A brief overview of serverless deployment using AWS Lambda
at AWS Re:Invent 2014, Werner Vogels the CTO at Amazon presented AWS Lambda with the amazing phrase “magic occurs in the interplay of events, functions and information.” As the phrase implies, AWS Lambda was initially designed to deploy events-driven services. The word “magic” because it is, as you’ll discover, AWS Lambda serves as an instance of serverless deployment technology. Europe Phone Number database providers
Serverless deployment technologies
The most popular cloud providers offer a serverless deployment choice but AWS Lambda can be the one that is most modern. Google Cloud has Google Cloud functions, which as of the time writing is in beta Microsoft Azure has Azure functions (https://azure.microsoft.com/en-us/services/functions). Europe Phone Number business database free download
Europe Phone Number b2b database
There are also open source serverless frameworks, such as Apache Openwhisk (https://openwhisk.apache.org) and Fission for Kubernetes (https://fission.io), that you can run on your own infrastructure. But I’m still not convinced about their worth. It is necessary be able to control your infrastructure for the framework. This does not sound exactly like serverless. In addition, as you’ll discover in the next section serverless is the programming model that is constrained that allows for minimal system administration. If you’re required to manage your infrastructure, you’re not getting the con-straints, but the benefits. buy Europe Phone Number database online
AWS Lambda supports Java, NodeJS, C#, GoLang and Python. Lambda functions are stateless service. It usually responds to requests by calling AWS services. For instance, a lambda function invoked when images are uploaded into an S3 bucket can insert the item into the DynamoDB IMAGES table , and send an update to Kinesis to initiate the processing of images. The lambda function could also call third-party web services. Europe Phone Number database providers
To run a service, you must package your application in JAR or ZIP file, then upload your application to AWS Lambda and provide what service to call to process requests (also known as events). AWS Lambda automatically runs enough instances of your microservice in order to handle any requests that come in. Each request is charged in accordance with the time it takes and the amount of memory used. Of of course, the devil’s in the details and, later, you’ll realize the fact that AWS Lambda has limitations. However, the idea that you as a developer or anyone within your organization has to worry about anything related to server, virtual machine or containers is an incredibly strong idea. Europe Phone Number database providers
Pattern: Serverless deployment
Use an automated server-less deployment system that is provided by a cloud public. Europe Phone Number database
Contrary to the other three patterns you will need a distinct programming model for your lambda function. The code of a lambda function and its packaging are dependent upon the language used to program. It is a Java lambda functions is an class which implements the general interface RequestHandler that was defined in the AWS Lambda Java core library and illustrated in the following list. The interface has two types of parameters I being the type of input and O that can be the output. The types that is used for I and O are dependent on the nature of the request that the lambda will handle.

Europe Phone Number database providers
An Java lambda functions is an instance of a class that implements RequestHandler interface.
public interface RequestHandler {
Public O handleRequest(I input Context context);
}
The RequestHandler interface provides the handleRequest() method. It has two parameters: one input item and the other a context that allow access to lambda’s execution context, like an ID for the request. HandleRequest() method produces the output objects. For lambda functions that handle HTTP requests that are proxied by an AWS API Gateway, I and O are APIGatewayProxyRequestEvent and APIGatewayProxyResponseEvent, respectively. As you’ll discover the handler functions are very similar to the old-fashioned Java EE servlets.
A Java lambda file is delivered as an ZIP file or a JAR file. JAR files are a JAR File is an super JAR (or large JAR) made through, for instance the Maven Shade plugin. The ZIP file contains classes that reside in the root directory as well as JAR dependencies within the libraries directory. Then, I’ll show you how the Gradle project can generate the ZIP file. First, let’s explore the various methods of calling the lambda function. Europe Phone Number database
Lambda functions invoked by lambda Europe Phone Number database providers
There are four methods to invoke a lambda function:
HTTP requests
Events that are generated by AWS services
Invocations scheduled for the future
Directly, using an API call. API call
Let’s examine each one.
STAFFING HTTP REQUESTS
A method to invoke the lambda function is to create your AWS API Gateway to route HTTP requests to your lambda. The API gateway will expose to your lambda by way of it is an HTTPS endpoint. It serves like the HTTP proxy, calling the lambda function using the HTTP request object. It then expects it to deliver with an HTTP reply object. Utilizing the API gateway in conjunction with AWS Lambda, you can implement, for example, RESTful services using lambda functions.
EVENTS HANDLING SUBMITTED BY AWS SERVICES Europe Phone Number business database free download

Europe Phone Number address lists
Europe Phone Number database free download
Another method to call the lambda function is set up your lambda function to take care of events caused from the AWS service. Examples of events that trigger a lambda function are the following: buy Europe Phone Number database online
The object is created within the S3 bucket.
A record is created, modified or deleted from the DynamoDB table.
A message can be read through the Kinesis stream.
An email message is sent through the Simple email service.
Because of this , and the integration to the other AWS products, AWS Lambda is useful for a myriad of tasks. Europe Phone Number database providers
SCHEDULED LAMBDA FUNCTIONS
Another method to call a lambda program is to utilize the Linux similar cron-like schedule. You can set up your lambda to be invoked frequently, such as every minute three hours or seven days. You can also use an cron expression to define the time when AWS will invoke your lambda. Cron expressions offer a lot of flexibility. For instance, you could set up a lambda that will be executed between 2:15 p.m. Monday through Friday. Europe Phone Number database
INVOKING A LAMBDA FUNCTION Using Web Service Request
The fourth method of calling the lambda function is to ask the application you are using to call it via web service request. A web request will specify the the lambda function, as well as input event information. Your application may invoke a lambda function either synchronously or asynchronously. If your application uses the lambda function in asynchronous manner then the response from the Web service’s HTTP response contains the lambda function’s response to the function lambda. In the other case, if it invokes the lambda function without synchronization the response of the web service indicates whether or not the lambda function was successful. buy Europe Phone Number database online
The benefits of lambda functions Europe Phone Number database
Lambda functions are used to deploy services. It offers several advantages:
Integrated with a variety of AWS services. It’s very easy to write lambdas which consume the events produced by AWS services, like DynamoDB and Kinesis and then handle HTTP requests through AWS API Gateway. AWS API Gateway.
Removes many tasks associated with system administration. You’re no longer accountable for low-level system administration. There aren’t any operating systems or runtimes that you need to patch. Therefore, you can work on your app.
Elasticity – AWS Lambda runs multiple instances of your application as required to manage the workload. It isn’t a problem of forecasting capacity needed or the chance of under- or over-provisioning containers or VMs.Europe Phone Number business database free download

Europe Phone Number database for sale
